Default Android Browser SOP bypass flaw
Rafay Baloch, security researcher has discovered a flaw in Android default browsers which, the potential hackers can use to steal sensitive data from open tabs/pages. The latest same-origin policy (SOP) bypass vulnerability is the second discovered by researcher Rafay Baloch, who discovered the first, CVE-2014-6041, last month.
Only Android default browsers affected
The vulnerability of same-origin policy (SOP) bypass affects only the default Android browser. The vulnerability is in how Javascript is handled by the Android function responsible for loading frame URLs. Normally in any browser, the SOP is prevents the JavaScript on one page or tab to from accessing data/content on another page/tab. But the Android browser has a flaw which enables a potentials hacker to bypass the SOP and read/collect data on the other tabs. In layman language if you have a tab/page open where you have filled your credit card details and you open the page with the JavaScript which has bypassed the SOP is opened, chances are that the hacker will be able to read the credit card details from the other open page.
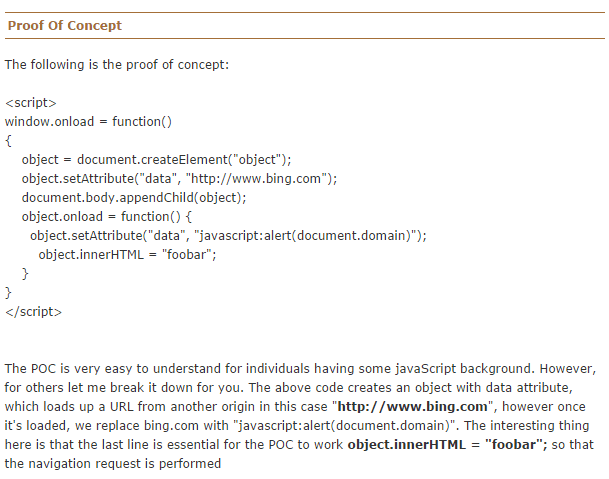
Proof of Concept
Rafay has published a Proof-of-Concept on his weblog to prove that the Android browsers are indeed vulnerable. The PoC is given below courtesy Rafay Baloch.
Rafay says in his blog, “Since, my recent android SOP bypass [CVE-2014-6041] triggered a lot of eruption among the infosec community, I was motivated to research a bit more upon the android browser, it turns out that things are much worse than I thought, I managed to trigger quite a few interesting vulnerabilities inside of Android browser, one of them being another Same Origin Policy Bypass vulnerability. The thing that makes it worse was the same SOP bypass was already fixed inside of chrome years ago, however the patches were not applied to Android browser < 4.4. “
SOP bypass flaw patched in Android KitKat 4.4 and above
Rafay says that Google has noticed the flaw and patched it in its latest operating system, the Android KitKat 4.4. But for strange reason it has not been patched in Android version below 4.4 by Google. In a separate post on ThreatPost, Google has stated that this vulnerability has been patched with the release for Android 4.1-4.3 aka Jellybean.
Older Android >4.4 users still vulnerable?
As said above, older Android users are still vulnerable to this major security threat. Google doles out latest Android versions on its stock edition handsets and tablets like Google Nexus etc. and many big manufacturers roll out the latest firmware to their flagship products but most of the smartphones and tablets in the markets are neither Google Play Edition devices nor flagships like Sony Z3 or Samsung Galaxy s5.
This flaw hits most of the users who are in lower middle and middle segment smartphone buyers. The vulnerability is a “major issue,” Ted Eull, vice president of mobile services for security vendor viaForensics, said.”Because the browser was included by default on many devices pre-KitKat (version 4.4), there are potentially hundreds of thousands of affected users,” he said.
Vulnerable Smartphones
Phones that are likely vulnerable include the Samsung Galaxy S3 , the Samsung Galaxy Note 2, and all mid-segment and low segment Samsung smartphones and tablets, the LG Optimus G, the LG G2 and all mid-segment and low segment LG smartphones and tablets and the Motorola Droid RAZR, Sony’s entire line of smartphones barring those which have been upgraded to Android 4.4 KitKat.
Thankfully, only the default Android browsers are affected by the SOP bypass vulnerability. If you use any Android smartphone / tablet which has an operating system earlier than Android 4.4 KitKat, it is advised that you surf the web via Chrome, Firefox or any other browser. If you have still not download Chrome or Firefox, you are suggested to download it now from Google Play Store and set THAT browser as your default one.
If you are using a rooted Android device, you should uninstall the default Android browser.
When asked to comment on this serious vulnerability and what they were doing to protect their customers, AT&T did not respond to a request for comment while Verizon Wireless pointed out that it has a website where customers can go to check whether updates are available for their phone.
“We regularly deliver software updates after thorough testing to ensure customers have a great experience,” Debra Lewis, spokeswoman for the company said.