Earlier this week the same group of Researcher exposed a critical Vulnerability in world’s most popular messaging App WhatsApp which allowed an Attacker to trace user’s location data
The researchers have found that there is a a serious security flaw in the way Viber receives and transmits images, Doodles, Video files as well as the way it sends or receives location data. Researchers have also found out that Viber stores data in an unencrypted format on their servers which is easily susceptible to tampering or hacker attack.
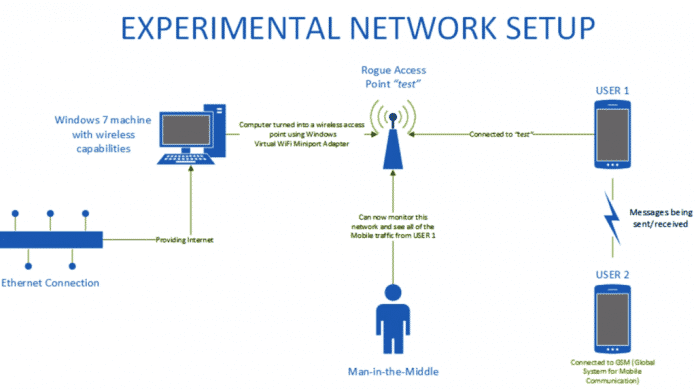
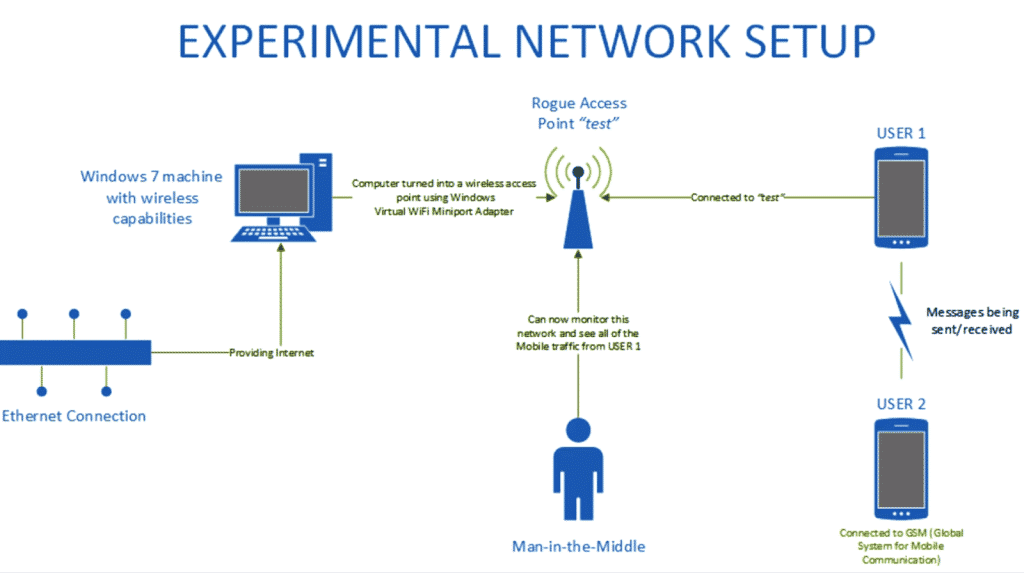
Any Network provider, attacker with a Rogue AP, or any man-in-the middle attack can take leverage of the flaw and can easily steal user’s data.
A video demonstration explaining how the Attack works can be seen below,
The mobile traffic was captured using the Windows 7 virtual wifi miniport adapter feature. The host computer was connected to the Internet via an Ethernet cable so that the wireless card was not in use. The Ethernet connection was set to share its Internet access with the virtual wifi miniport adapter. researchers were now able to capture the traffic over the network test using various tools such as NetworkMiner, Wireshark, and NetWitness.
Anyone, including the service providers will be able to collect this information – and anyone that sets up a rogue AP, or any man-in-the middle attacks such as ARP poisoning will be able to capture this unencrypted traffic and view the images and videos received as well as the locations being sent or received by a phone. the researchers said in a blog post
The Flaw was reported to the Viber security team, however no response was heard back by the researchers.