HTC vulnerable to fingerprint stealing, stores fingerprint image files in unencrypted folder
Looks like the troubled times for HTC is not over. Earlier this month, HTC reported its worst quarter in history. If that was not enough, FireEye researchers last week discovered that HTC was storing high-resolution images of your fingerprints directly on your Android phone with little security.
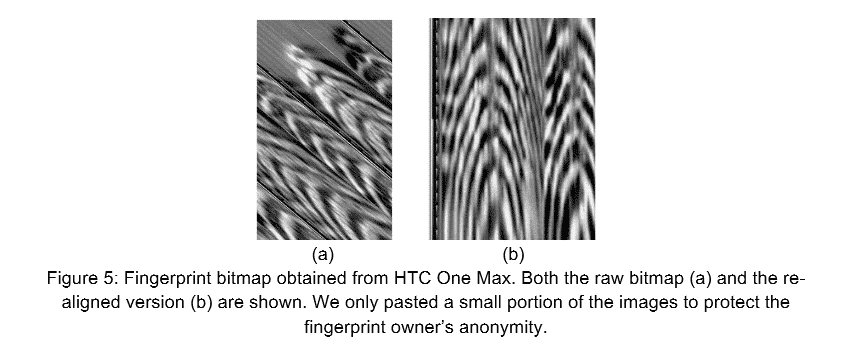
In a white paper released by FireEye researchers(PDF), the group mentioned how easy it was to recover the image files from an HTC One Max phone. The fingerprints were stored in an image file named dbgraw.bmp in an open, readable and unencrypted folder.
“Not all the vendors store the fingerprints securely. While some vendors claimed that they store users fingerprints encrypted in a system partition, they put users fingerprints in plaintext and in a worldXreadable place by mistake. One example is HTC One Max XX the fingerprint is saved as /data/dbgraw.bmp with 0666 permission (worldXreadable).”
This means anyone that gains access to these files is capable of editing the fingerprints, deleting them and even forcing fake fingerprint scans.
The FireEye team also added “Any unprivileged processes or apps can steal a user’s fingerprints by reading this file.” This means the image would get updated every time in that world readable folder, every time the fingerprint sensor would be swiped to unlock the device. As a result, a malicious process could steal multiple images without detection.
HTC fixed the bug
The bug was fixed by HTC after FireEye notified the company of how dangerous it was.
Talking about other security faults in Android, the researchers said that even if the protection of fingerprint data in a so-called “TrustZone” is indeed trustworthy, it only means that the fingerprints previously registered on the devices are secured.
“We found that the fingerprint sensor itself in many devices is still exposed to the attackers. Although the ARM architecture enables isolating critical peripherals from being accessed outside TrustZone (e.g. by programming the TrustZone Protection Controller), most vendors fail to utilize this feature to protect fingerprint sensors”.
The research was presented at the BlackHat conference in Las Vegas last week by Yulong Zhang, Zhaofeng Chen, Hui Xue, and Tao Wei of FireEye Labs.
Apple which pioneered the modern fingerprint sensor is “secure enclave”, as it encrypts fingerprint data from the scanner and never saves the actual image. Hence, it is impossible to retrieve a scan of the fingerprint. However, a group showed how by using a silicon representation of a stolen fingerprint they could successfully break into an iPhone.
With the researchers predicting that fingerprint scanners will exist in about 50 percent of the phones sold in 2019, it is even more frightening to think of the lack of security on some devices with scanners. It is unfortunate that many of the phone manufacturers are not serious about the security of your biometrics and it is very difficult to find out what exactly are they doing with your fingerprint data or is it being kept safe.

Very quickly this web page will be famous amid all blogging visitors,
due to it’s good content