Hackers have become relentless in targeting businesses these days. The customer and financial data that you process and store in your computers are now a goldmine for hackers to steal. Personal records and payment information can be sold for profit over the black market. Hackers are even utilizing various methods to compromise networks and infrastructure infrastructures.
As such, organizations may have to go beyond conventional security tools like antiviruses and firewalls and implement security measures that can detect and combat advanced attacks. But before you go about adopting virtually every available solution that’s being offered today, it’s only practical to test your defenses and establish a baseline of what’s really needed.
To do this, you can perform conventional methods like penetration tests but these require technical know-how to perform, making them out of reach to smaller and less-resourced organizations. Fortunately, breach and attack simulation (BAS) platforms like Cymulate are now emerging to allow organizations of all sizes to assess their security posture through automated penetration tests and identify if there are vulnerabilities that need to be immediately addressed.
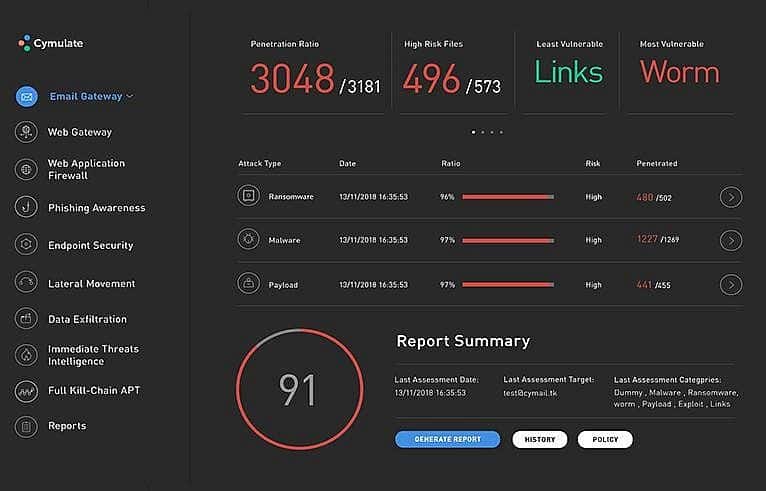
These platforms can automatically run simulation tests to see the effectiveness of the security measures that a business has placed to protect its infrastructure. BAS tools also give corrective suggestions so that you can quickly plug the security gaps in your infrastructure.
Given the number of cyberattacks, implementing security measures is not enough. Companies must remain vigilant and must regularly check their defenses to ensure maximum protection against threats.
Attacks can come from anywhere
Hackers now have access to various tools and methods to break into systems. Trojans and malware continue to be among the most popular means they steal data from company servers. They can be introduced to networks in a variety of ways.
Mainly, hackers rely on social engineering attacks like phishing to trick company staff into downloading and installing malware on their computers. Attackers can also try to brute force their way into networks. Poorly secured endpoints, weak passwords, and password reuse can all be exploited by attackers to easily gain remote access to computers and network devices.
There has also been a resurgence of ransomware attacks in 2019 and SMBs are among the most affected by the threat. Managed Service Providers (MSPs) say that 56 percent of their clients from small-to-medium businesses (SMBs) experienced a ransomware attack.
Even digitization and digital adoption efforts can inadvertently expose you to cyberattacks. Software and applications can have zero-day vulnerabilities that hackers can exploit. Zero-day vulnerabilities are typically addressed in timely security patches. However, software vendors are sometimes not quick enough to release patches to counter the attacks. Users can also be remiss in applying these patches.
How BAS can help
To protect against these methods, companies must implement various measures and use different security solutions and tools. Firewalls can prevent malicious traffic from reaching the network. They can also prevent suspicious outgoing traffic like data exfiltration attempts to be sent out. Endpoint security like antiviruses and antimalware can prevent malware from executing and spreading to other computers. Even users must be tested to see how well they react to phishing attacks.
BAS platforms can help you evaluate the security of these potential attack vectors. Cymulate can run simulation scripts that can test the capabilities of implemented solutions such as firewalls and antiviruses in a network. The platform can check a company’s web application firewall if it can block payloads from performing malicious actions. In addition, it can simulate ransomware, trojans, and worms on a dedicated endpoint to check if antiviruses can properly detect and remove these threats.
Cymulate can also test how an organization will react to phishing attacks. It can simulate phishing scams and send emails to everyone in the organization. The platform can readily track which members of the team opened the message and failed to identify the malicious emails. Email templates can even be customized in order to further cleverly disguise these simulated phishing messages much like how hackers now heavily personalize the actual emails that they send.
Cymulate can provide a comprehensive assessment of a security system with numerical scores on how well security measures perform against various attacks. It even provides actionable insights to help you prioritize when addressing vulnerabilities in your network and improving your security posture.
The high cost of attacks
Falling victim to a cyberattack can have grave effects for small businesses. Malware attacks such as ransomware can deny user access to files and computer systems unless a ransom is paid. Losing access to company files and critical customer information can halt regular business operations resulting in prolonged downtime, which can result in significant financial losses. As such, many businesses are forced to pay the ransom. In 2018, the average ransom demand was more than $116,000.
Security breaches can also mean potential lawsuits against businesses. Customers that had their data compromised can sue the company. This does not only mean expensive legal fees but it can also damage an organization’s reputation and may cause client-customer fallouts. In addition, stringent privacy and data protection regulations can impose fines on negligent companies.
Recovering from an attack is also costly for any business. Small businesses that fall victim to cyberattacks can spend over $50,000 dealing with the fall out and take months to recover. Unfortunately, many small businesses fail to sustain their business after an attack.
In fact, 60 percent of small companies that suffer from a data breach are forced to effectively close shop within six months.
Reinforcing Your Defenses
This is why it’s critical to determine how well your security measures work and BAS offers the means to comprehensively test multiple vectors.
Through stringent testing, you can immediately perform corrective actions like replacing tools that performed poorly against simulated attacks. Antiviruses that were incapable of detecting BAS dummy payloads can be replaced with more capable measures. Firewall rules can be adjusted to be more stringent. You can even institute training programs for employees to improve their security skillsets.
No security measure can guarantee a breach-free network, but using BAS can obviously help businesses beef up your defenses. Ensuring the effectiveness of security tools and the readiness of personnel to threats can establish a robust security system that can better protect your organization from modern attacks.
