The alarming hacking incident that targeted a water treatment facility in Florida is one of the more recent real-world proof for the need for more meticulous cybersecurity. Nobody is safe from cyber attackers. From businesses to government facilities, hackers and other bad actors attack whenever they see a vulnerability or opportunity.
Today’s antiviruses or malware protection software have become more sophisticated, as they include new features and functions such as the ability to scan links and email attachments, block spyware, and check for system weaknesses that may be exploited by cybercriminals. Still, they are not enough to provide adequate protection. That is why organizations put in place many other security solutions including firewalls, endpoint detection and response (EDR), security web gateway, VPN, and network access control (NAC), among others.
Running multiple cybersecurity tools is inevitable and often necessary, since it is difficult to find a single security solutions provider that reliably covers all the security concerns of organizations. The problem with this is that the many tools deployed may not be put to their optimum utility if they are not unified. They are unlikely to provide the desired security visibility necessary to keep an organization protected against the latest threats, vulnerabilities, and anomalous network activities.
For this, it helps to use a platform that efficiently and seamlessly unifies and centralizes all your cybersecurity solutions. Cyrebro, a managed security operations center (SOC), significantly boosts cybersecurity visibility across an organization by unifying the various security products and platforms used.
Organizing chaos
It is not easy to keep track of all the alerts and notifications from several security solutions. More so, it is challenging to respond appropriately to specific security alerts when they come by the thousands.
A Forrester study found that an average security operations team receives more than 11,000 security alerts in a day. This means more than 450 alerts per hour if security teams were to work for 24 hours in a day. Evaluating the alerts and deciding on the best action in dealing with them is not only going to be tedious, but also likely to be prone to mistakes.
It is not unexpected that many organizations decide to be less meticulous in dealing with these security alerts. Some even resort to automatically selecting default actions or even randomly deciding on what to do with them, resulting in inefficiencies and a weakened security posture. The large number of notifications or security threat signals received through various security solutions can become chaotic. They can create an unoptimized cybersecurity protocol.
Companies with complex organizational setups employ several cybersecurity solutions. Those that operate using hybrid systems use different security software tools including cloud access security brokers (CASB) like Oracle CASB Cloud, Stratokey, and FortiCASB.
A central platform for security operations organizes all security event information to facilitate prompt response, the plugging of vulnerabilities or weaknesses, and accountability across the security network. It enables strategic monitoring and threat hunting to optimize an organization’s cyber defenses. Additionally, it supports effective forensic investigation.
Integrating security solutions
It is possible to gather all the security event data collected from various security solutions used in an organization by integrating them under one platform. Integration helps avoid cybersecurity siloing or the fragmentation of information and functions. Fragmented or decentralized setups are preferred in some situations, but not in enterprise cybersecurity. As a CMMI Institute paper suggests, decentralization has its place in the security ecosystem, but centralization is necessary to achieve coherence, coordination, and comprehensive security visibility.
Enhanced threat intelligence and response
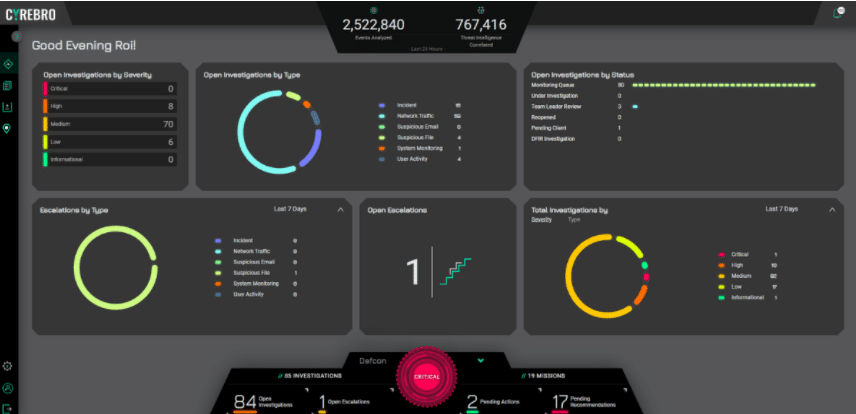
Integration enables more powerful threat intelligence and threat hunting. As Cyrebro’s centralized security dashboard demonstrates, security teams get a better view of critical incidents across business operations and the security solutions deployed in different departments or even geographical locations.
With the help of artificial intelligence, cross-organization learning in particular, security events are analyzed and sorted according to their gravity. This allows security teams to see the most critical security concerns that need to be addressed as soon as possible. Additionally, it enables the monitoring of security solutions that are running to ensure an organization’s cyber defense and the tracking of endpoints that connect to an organization’s network.
Also, centralizing threat intelligence yields easy-to-understand reports almost instantly, allowing security teams and other involved parties to have quick access to actual information at specific moments of inspection.
Moreover, the centralization of security solutions can potentially allow security teams to even have a “global” view of the state of security of an organization. Going back to the Cyrebro example, this centralized SOC comes with a “Host Index and Maps” feature, which provides a graphical view of the different endpoints of an organization around the world. It collects and presents security data from the different laptops, desktops, mobile devices, and servers that connect to the enterprise network.
The takeaway
The hacked water treatment facility in Florida had all the basic cybersecurity controls. There were no reported issues of defective malware protection and lack of software updates. The hack happened because of a remote access vulnerability exploited by the attackers and the common human weakness of being cavalier when it comes to passwords. All of these could have been detected and addressed if the IT team had comprehensive security visibility through a cybersecurity centralization platform.
Regardless of the size of an organization, defects or weaknesses in security protocols and defensive measures cannot be completely eliminated. Thus, it is essential to have an expanded view of the security events and statuses across an organization for security teams to see vulnerabilities others may miss at specific endpoints. This centralized and unified approach empowers strategic threat monitoring and a better security posture in general.

