The report which was released today by Kaspersky lab expert includes the in depth analysis from the leak which was published earlier this week on the Mt. Gox CEO’s blog, after it was hacked.
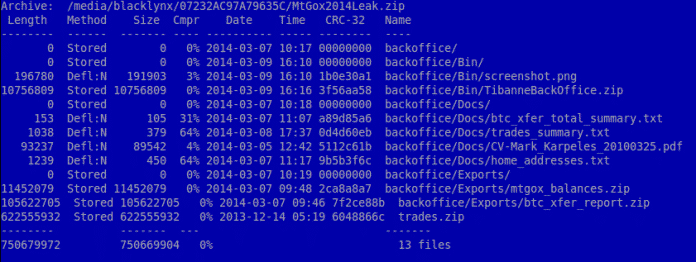
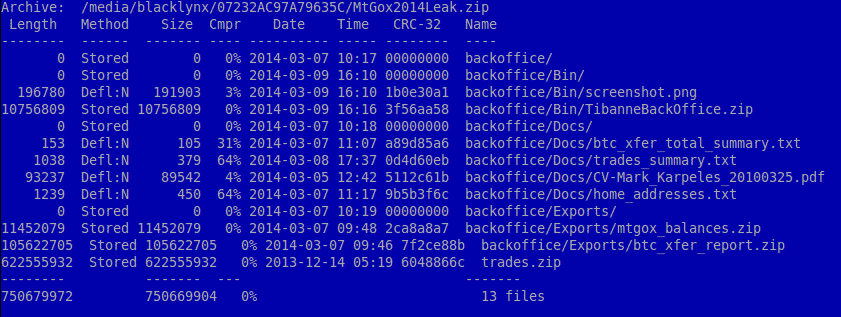
MtGox2014Leak.zip a 716 Mb Archive which the hackers claimed to contain valuable database dumps and specialized software for remote access to MtGox data is nothing more than a malware created to search and steal Bitcoin wallet files from the potential victims. The Reddit posters had warned against downloading the said file at that point of time and seems that it was a wise advise which we at techworm had wholeheartedly endorsed.
The Zipped Archive contains different data including a 620 Mb file “trades.zip”, the biggest of all other files. In fact this file is a publicly available data on MtGox trades. What is really interesting is the Archive contain software binaries for Window PC and Mac.
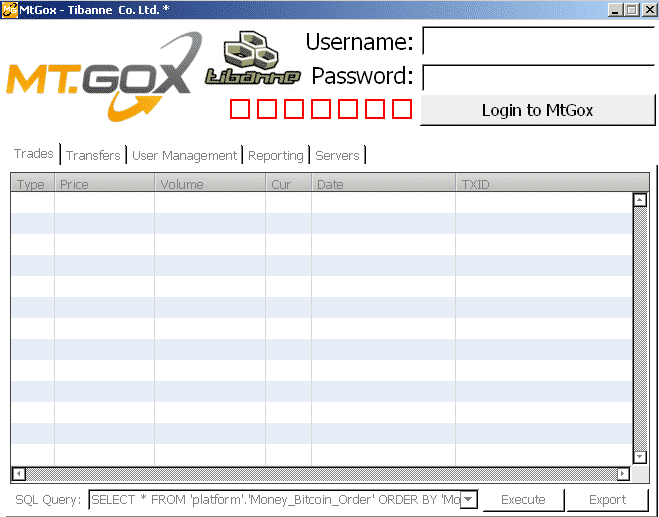
The Executable file which tricks user into believing that they are seeing databases of Mt. Gox’s owning company, Tibanne Co. Ltd., is in fact”Trojan.Win32.CoinStealer.i”.
The file when executed creates and executes the TibanneSocket.exe binary and searches for the files bitcoin.conf and wallet.dat and sends it to remotely located command and control server. Kaspersky have managed to locate of the C & C server and found it to be in Bulgaria. The server was offline at the time of writing of this article. Since most people are curious to see the leaked data, the trojan creator smelled a opportunity and released the malicious code through the binaries. It was reported by Kaspersky that the creator was actually successful in spreading the malware though it could not be ascertained whether the attacker managed to remotely access any of the victims bitcoin wallets.
Indepth Analysis of the Malware can be seen from the Securelist blog