Cybersecurity researchers at Google’s Mandiant Threat Defense have uncovered active exploitation of an unauthenticated access vulnerability within Gladinet’s Triofox platform — a tool businesses use for secure file sharing and remote access.
The critical bug, tracked as CVE-2025-12480 (CVSS score: 9.1), allows attackers to bypass authentication, access internal setup pages, and execute malicious code on affected systems. While Gladinet released a patch back in June 2025, Mandiant says threat actors were seen exploiting unpatched servers as recently as August 2025.
A Clever Exploit Chain
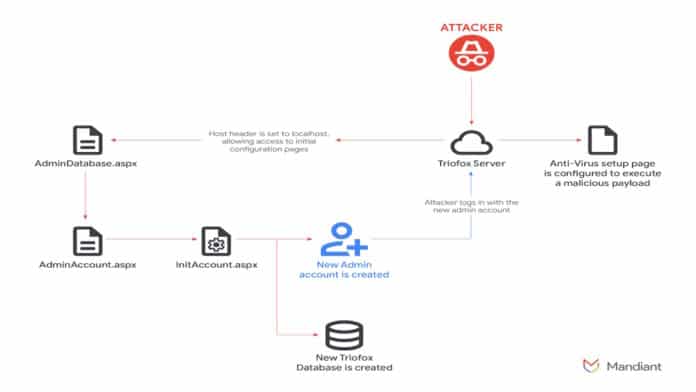
According to Mandiant, the threat group behind the attacks, tracked as UNC6485, took advantage of the flaw to create a new native admin account called “Cluster Admin,” gaining full system privileges. From there, they abused Triofox’s own built-in antivirus feature — normally designed to protect systems — to run malicious code with SYSTEM-level privileges.
“To achieve code execution, the attacker logged in using the newly created Admin account. The attacker uploaded malicious files to execute them using the built-in antivirus feature,” security researchers Stallone D’Souza, Praveeth D’Souza, Bill Glynn, Kevin O’Flynn, and Yash Gupta wrote in a blog post.
“To set up the antivirus feature, the user is allowed to provide an arbitrary path for the selected anti-virus. The file configured as the antivirus scanner location inherits the Triofox parent process account privileges, running under the context of the SYSTEM account.”
By reconfiguring the antivirus path to point to their own script, execute it automatically, giving them deep control over the host system. The malicious script, called centre_report.bat, downloaded from a remote IP (84.200.80[.]252) and installed a legitimate Zoho Unified Endpoint Management System (UEMS) package. Using that installer, hackers then deployed Zoho Assist and AnyDesk — popular remote access tools that let them take full remote control of the compromised servers.
What The Hackers Did Next
Once the hackers had administrative control, the attackers used Zoho Assist to perform reconnaissance, change user passwords, and add existing accounts to local and domain administrator groups to expand their access. To maintain access, they also deployed Plink and PuTTY — two legitimate SSH networking tools — to create an encrypted tunnel that allowed covert Remote Desktop (RDP) access over port 433.
This method effectively masked their communication with command-and-control (C2 or C&C) servers, making detection more difficult for defenders.
Patching And Recommendations
Gladinet has already fixed the flaw in Triofox version 16.7.10368.56560 on July 26, but Mandiant urges users to upgrade immediately to the latest available release if they haven’t already. The firm also recommends that system administrators:
- Audit all admin accounts for suspicious and unauthorized additions like “Cluster Admin.”
- Check antivirus settings to ensure they aren’t configured to execute external scripts.
- Monitor for unusual SSH or RDP traffic, which could indicate covert remote access.
“Security teams should also hunt for attacker tools using our hunting queries listed at the bottom of this post, and monitor for anomalous outbound SSH traffic,” concludes the report.
This is the third Triofox vulnerability to be exploited in the wild this year, following CVE-2025-30406 and CVE-2025-11371. The string of incidents underscores how quickly attackers are moving to weaponize patched flaws into opportunities to target unpatched systems.