Eloi Vanderbeken, a security researcher from synacktiv.com had discovered a backdoor in several models of Linksys, Cisco and Netgear Wi-Fi DSL modems that would grant admin access to the attacker along with the ability to reset the router’s configuration. After Vanderbecken published his findings and several others corroborated his results in January 2014, the modem manufacturers like Netgear and other vendors published a new version of the firmware that was supposed to close the back door. Now Vanderbeken has found that the firmware released by the vendors is just a camouflage. As per a report by Arstechnica, the new firmware does not ‘fix’ the backdoor. It merely hides it.
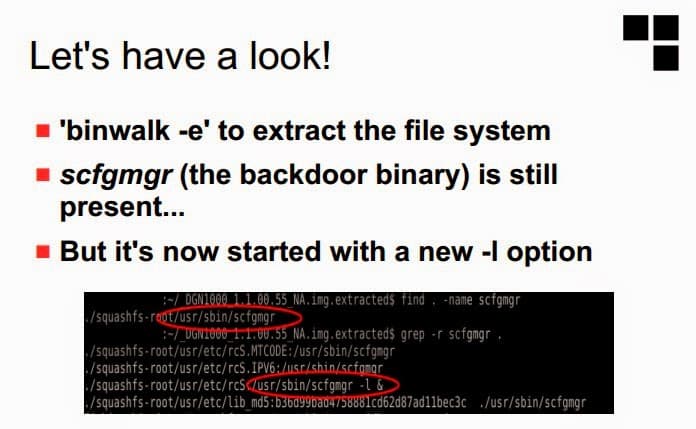
Vanderbeken found out that the new firmware apparently only hid the backdoor rather than closing it. In a PowerPoint presentation posted by him on April 18, Vanderbecken has now confirmed that that the “fixed” code concealed the same communications port he had originally found (port 32764) until a remote user employed a secret “knock”—sending a specially crafted network packet that reactivates the backdoor interface.
The packet structure used to open the backdoor, Vanderbecken said, is the same used by “an old Sercomm update tool”—a packet also used in code by Wilmer van der Gaast to “rootkit” another Netgear router. The packet’s payload, in the version of the backdoor discovered by Vanderbecken in the firmware posted by Netgear, is an MD5 hash of the router’s model number (DGN1000).
The nature of the change, which leverages the same code as was used in the old firmware to provide administrative access over the concealed port, suggests that the backdoor is an intentional feature of the firmware and not just a mistake made in coding. “It’s deliberate” Vanderbecken asserted in his presentation.
Readers may note that many users reading the initial results of Vanderbeken in January, 2014 had concluded or alluded that the DSL modem manufacturers kept the backdoor specifically for NSA. Though this has never been proved or accepted either by NSA or the modem vendors, Vanderbeken’s new research seemingly points towards a deliberate masking of the backdoor by the high profile vendors for reasons best known to them. The manner in which the so called patch was supposed to ‘fix’ the backdoor only highlights the doubts of the users and readers towards a company authorised backdoor.
In all 24 models of Wi-Fi DSL modems are said to have the above backdoor. Among the 24 models the below listed models are top selling modems in the world.
– Linksys WAG200G
– Netgear DM111Pv2
– Linksys WAG320N
– Linksys WAG54G2
– DGN1000 Netgear N150
– Diamond DSL642WLG / SerComm IP806Gx v2 TI