Just a month after the revelation of a severe vulnerability in OpenSSL called the #Heartbleed which led to hundreds of websites taking preventive action as well as resetting user passwords, the OpenSSL project has reported fixes for several vulnerabilities out of which at least one of them has been categorised as very serious.
The OpenSSL project has issued advisories for 3 user updates which are given below :
OpenSSL 0.9.8 DTLS users should upgrade to 0.9.8za
OpenSSL 1.0.0 DTLS users should upgrade to 1.0.0m
OpenSSL 1.0.1 DTLS users should upgrade to 1.0.1h
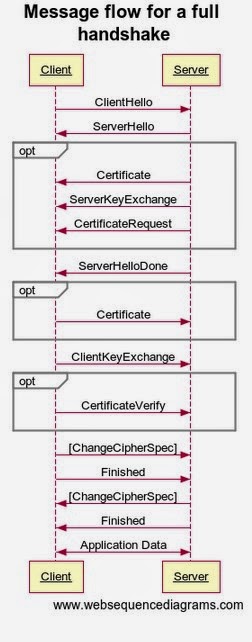
Out of the three fixes the most import fix is for the SSL/TLS MITM vulnerability (CVE-2014-0224). This vulnerability was discovered by Kikuchi Masahi of Lepidum Co. Ltd. Kikuchi first reported the bug on his blog. In Kikuchi’s own words “The problem is that OpenSSL accepts ChangeCipherSpec (CCS) inappropriately during a handshake. This bug has existed since the very first release of OpenSSL.” The vulnerability is so severe that it effects all versions of OpenSSL, including those that were patched to fix Heartbleed.
All client versions of OpenSSL are vulnerable. OpenSSL servers are only known to be vulnerable in versions 1.0.1 and 1.0.2-beta1. The bug was discovered by KIKUCHI Masashi (Lepidum Co. Ltd.) and reported to OpenSSL on May 1 via JPCERT/CC. Kikuchi has published his own explanation of the bug.
Resources :
1. Lepidum Blog