‘Press enter key’ exploit reveals major Linux security hole gaps
A critical and easy to exploit vulnerability discovered in many of the Linux distros has put millions of users at risk. Hector Marco, lecturer at the University of the West of Scotland and Ismael Ripoll, assistant professor in Polytechnic University of Valencia found that CVE-2016-4484 (Cryptsetup Initrd root Shell) affects the Cryptsetup script that is used to unlock partitions encrypted with LUKS (Linux Unified Key Setup).
LUKS is the standard device for executing Linux hard disk encryption. LUKS is often put into action with Cryptsetup. The problem lies in the Cryptsetup default configuration file, which is a bad one. Known Linux distributions with this bug include Debian, Ubuntu, Fedora, Red Hat Enterprise Linux (RHEL), and SUSE Linux Enterprise Server (SLES).
Details of the vulnerability were revealed by Hector Marco and Ismael Ripoll, who explain:
This vulnerability allows to obtain a root initramfs shell on affected systems. The vulnerability is very reliable because it doesn’t depend on specific systems or configurations. Attackers can copy, modify or destroy the hard disc as well as set up the network to exflitrate data. This vulnerability is specially serious in environments like libraries, ATMs, airport machines, labs, etc, where the whole boot process is protect (password in BIOS and GRUB) and we only have a keyboard or/and a mouse.
Note that in cloud environments it is also possible to remotely exploit this vulnerability without having physical access.
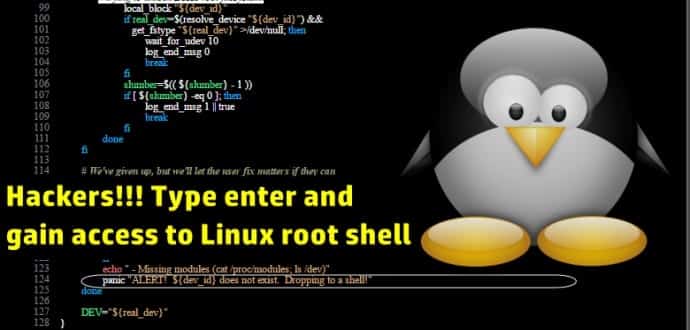
The researchers found out problems in how Cryptsetup scripts handle the boot process when the user is asked for the encryption password. This password is needed to decrypt information on protected hard drives, boot the system, and grant the valid user access to his data.
“The fault is caused by an incorrect handling of the password check in the script file /scripts/local-top/crypt rot,” Marco explains. “When the user exceeds the maximum number of password tries (by default 3), then boot sequence continues normally.”
Marco says that Cryptsetup understands this error as a “slow device” that needs more time to warm-up. Due to this design error on the developer’s part, Cryptsetup allows the user to retry his encryption password by reloading the authentication process.
This procedure is reloaded up to 30 times on an x86 system (93 total password tries), and 150 times on a PowerPC machine (452 total password retries).
However, the good news is that the problem is incredibly simple to fix. Marco and Ripoll have developed a patch and a workaround that will mitigate the attack.
According to the pair, the vulnerability could have been introduced when other security fixes were implemented.