Security researchers at Palo Alto Networks’ Unit 42 have uncovered a stealthy spyware campaign, which used WhatsApp images to exploit a hidden Samsung flaw in Galaxy phones secretly.
The newly discovered Android spyware, dubbed LANDFALL, silently infiltrated Samsung Galaxy phones for months by exploiting a zero-day flaw in the company’s Android image-processing library, which allowed attackers to take control of a device the moment a malicious image was received with no clicks required.
According to the security researchers, the attacks began as early as July 2024 and targeted Galaxy users in the Middle East, including Turkey, Iran, Iraq, and Morocco.
A Hack Hidden In A Picture
Tracked as CVE-2025-21042, the attackers weaponized a critical vulnerability found in Samsung’s libimagecodec.quram.so library, which handles image files. This flaw allowed hackers to execute code remotely just by sending a malicious image through messaging apps such as WhatsApp, without the user clicking or downloading anything.
The moment the image was received, the device could be compromised — a so-called “zero-click” attack. The booby-trapped files looked like ordinary photos but were actually specially designed Digital Negative (DNG) image files with hidden code attached.
What The Spyware Could Do
Once opened or even previewed, they secretly launched the LANDFALL spyware, which turned affected phones into powerful surveillance tools. It could:
-
- Record microphone audio and phone calls
- Track GPS location in real time
- Access photos, messages, contacts, call logs, and browsing history
- Evade antivirus scans and remain active even after reboots
Researchers say the spyware targeted Samsung’s top models — the Galaxy S22, S23, S24, and the foldable Z Fold 4 and Z Flip 4 — until 2025. The latest Galaxy S25 series was not affected.
Long Exposure, Slow Fix
Evidence shows the campaign began in July 2024, yet Samsung did not release a patch until April 2025, leaving devices exposed for almost ten months. The flaw was patched only after Unit 42 privately disclosed it, though Samsung has not yet commented publicly on the findings.
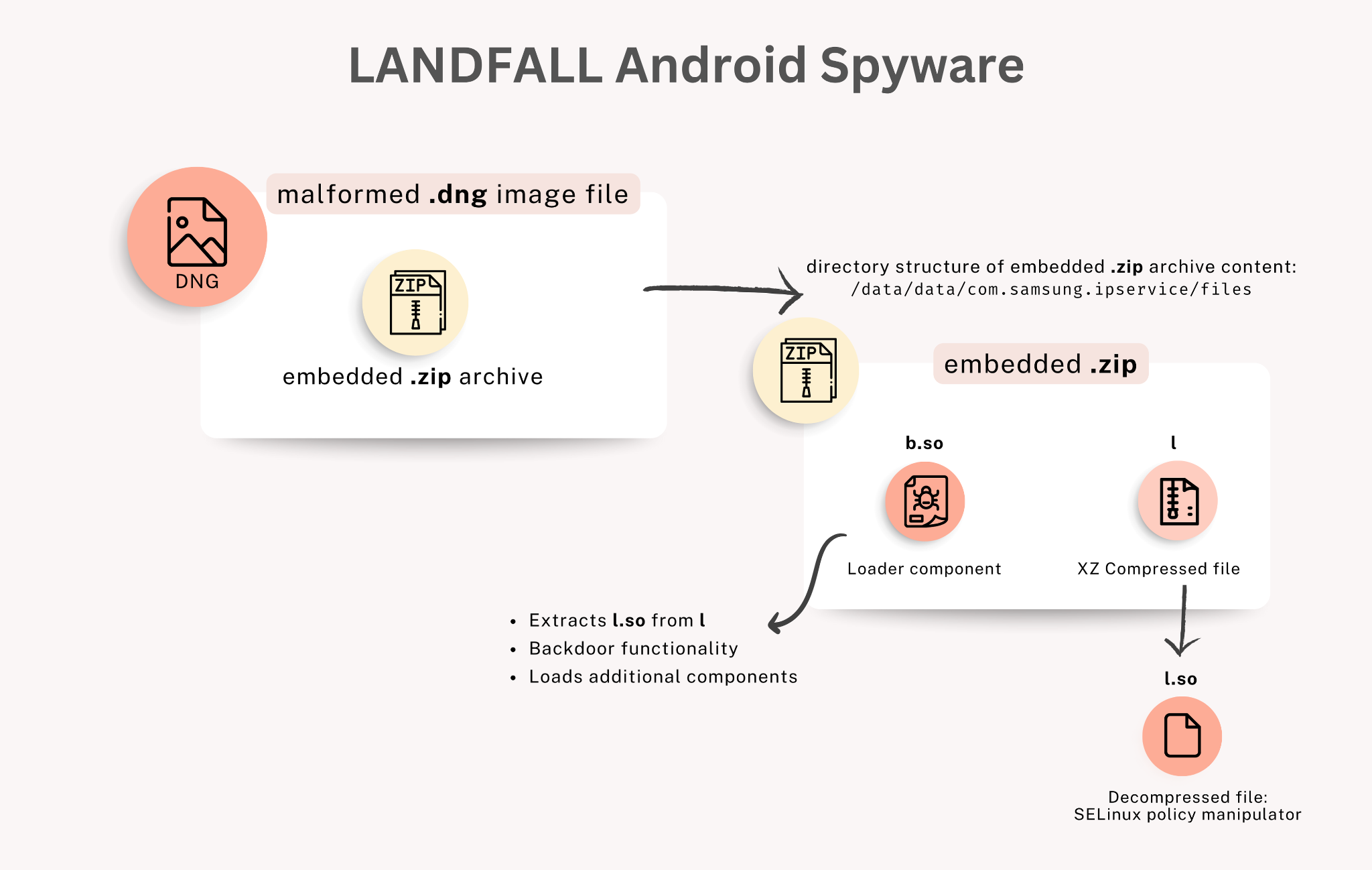
“The malformed DNG image files we discovered have an embedded ZIP archive appended to the end of the file. Figure 1 shows one of these samples in a hex editor, indicating where the ZIP archive content begins near the end of the file,” Palo Alto Networks wrote in its report.
“Our analysis indicates these DNG files exploit CVE-2025-21042, a vulnerability in Samsung’s image-processing library libimagecodec.quram.so that Samsung patched in April 2025. The exploit extracts shared object library (.so) files from the embedded ZIP archive to run LANDFALL spyware. Figure 2 below shows a flowchart for this spyware.”
Unit 42’s analysis revealed that the infected images carried two malicious components:
-
- b.so (“Bridge Head”) – a loader that downloaded additional spyware modules.
- l.so – a component that modified Android’s SELinux security settings to gain root access and maintain persistence.
While Samsung fixed CVE-2025-21042 in its April update, the company did not acknowledge that the flaw was being exploited. However, Palo Alto researchers later confirmed that LANDFALL attackers had been abusing the vulnerability since at least July 2024, months before the patch.
A Growing Trend Of Image-Based Exploits
The LANDFALL case is part of a broader rise in attacks that exploit image-processing vulnerabilities. In recent months, similar vulnerabilities have been discovered in both Android and iOS devices — including a chain of exploits involving Apple’s CVE-2025-43300 and WhatsApp’s CVE-2025-55177.
Samsung itself disclosed another zero-day (CVE-2025-21043) in September 2025, again tied to image-handling components across mobile ecosystems.
“While it was not exploited in the Landfall samples we discovered, the similarities between the exploit for Landfall (CVE-2025-21042) and this vulnerability (CVE-2025-21043) are striking. Both vulnerabilities were publicly disclosed around the same time and both are connected to DNG image file processing delivered through mobile communication applications,” Palo Alto Networks added.
How To Stay Protected
Security experts recommend that Samsung users running Android 13–15 install the April 2025 security updates or later, disable automatic media downloads in messaging apps like WhatsApp and Telegram, and enable Android’s Advanced Protection mode or iOS’s Lockdown Mode for high-risk users.