Table Of Contents
A complete tutorial for accessing the Dark Web using Tor on Linux, Mac and Windows PCs
The Deep Web (or Invisible web) is the set of information resources on the World Wide Web not reported by normal search engines, according a raw estimation of some security experts clear web represents only a small portion of the overall web content, the remaining part is unknown to the majority of web users.
Ordinary web users are literally shocked when understand the existence of the Deep Web, a network of interconnected systems, not indexed, having a size hundreds of times higher than the current web, around 500 times.
As the name suggests, the Dark Web is an extremely large and hidden portion of the internet, and this guide will help you to access it in a very ‘simple to follow’ guide. Let us start.
Getting started
In order to access the Dark Web, you will be required to download and installed a browser called Tor. While it is compatible with both Windows and Mac OS X, we will not be recommending you to use these platforms, and for very good reasons, which is security and of course privacy. The damage being inflicted on your operating system in the form of bugs is going to be extremely detrimental, not to mention that you might become the target of government officials, so make sure that you know what you are getting yourself into. Also, it is recommended that you are running the latest version of Mozilla Firefox, since it uses up less resources of your system and also blows up less number of whistles as far as privacy is concerned.
Download the official application
It is imperative that you read this very carefully. Do not download Tor from any other download site, and we highly recommend that you take the installation file from the official website. After you have downloaded the software, you can wish to test its legitimacy with the Tor Project’s GPG signatures as per the method below.
How to identify the legitimacy of a Tor browser download
You have to be careful every step of the way so here are the necessary steps that you should take in order to check if the software is legitimate or not.
Save the GPG signatures to the same directory as the Tor download and using these tools you can use the following process. Keep in mind that this is going to be for both the Mac and Linux platforms. Make sure that you have GPG Tools for Mac installed and GnuPG for Linux installed. Now, follow the steps given below (keep in mind that you will see the term ‘DownloadLocation’ at various locations of the guide. Replace this with the actual location of your download to avoid unnecessary obstacles standing in your way).
1. Import the public key of the Tor project (type in the same manner):
2. gpg –keyserver x-hkp://pool.sks-keyservers.net –recv-keys 0x4E2C6E8793298290
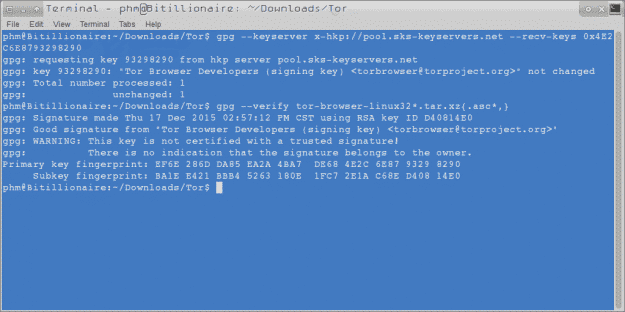
3. Verify on Linux using the following command: gpg –verify ~/DownloadLocation/tor-browser-linux*.tar.xz{.asc*,}
4. Verify on Mac using the following command: gpg –verify ~/DownloadLocation/TorBrowser-VERSION-osx*_en-US.dmg{.asc*,}
The results should look something like the image below:
For Windows, it is going to be a little trickier so be sure to follow the steps without missing anything
1. Get GPG for Windows. The files can be obtained from here
2. Fire up windows command prompt, or cmd (opening as Administrator is recommended)
3. Import the Tor Project signature: “C:\Program Files\Gnu\GnuPg\gpg.exe” –keyserver x-hkp://pool.sks-keyservers.net –recv-keys 0x4E2C6E8793298290
4. To verify the signature using GPG for Windows: “C:\Program Files\Gnu\GnuPg\gpg.exe” –verify C:\DownloadLocation\torbrowser-install-VERSION_en-US.exe.asc
C:\DownloadLocation\torbrowser-install-VERSION_en-US.exe
5. Keep in mind that all this process has to be carried out through cmd, or command prompt.
How to successfully install Tor on various operating systems
Here is how you will successfully be able to install the Tor browser on various platforms. Let us begin.
Linux (Debian based systems)
You will have the option of installing the Official Tor Repository and downloading it directly. This will save time and verification will be done automatically for you.
Debian: nano /etc/apt/sources.list
Insert: deb https://deb.torproject.org/torproject.org jessie main deb-src https://deb.torproject.org/torproject.org jessie main
Next, do the following:
Ctrl+O
apt-get update
apt-get install tor
Ubuntu
nano /etc/apt/sources.list
Insert: deb https://deb.torproject.org/torproject.org trusty main deb-src https://deb.torproject.org/torproject.org trusty main
Ctrl+O
apt-get update
apt-get install tor
Mac
1. Download and install Macports from here
2. Next, open a terminal and type the following command: sudo port install tor
Windows
Installing the Tor Browser to access the Dark Web on Windows is the simplest process possible. Just install the program like you would any other program.
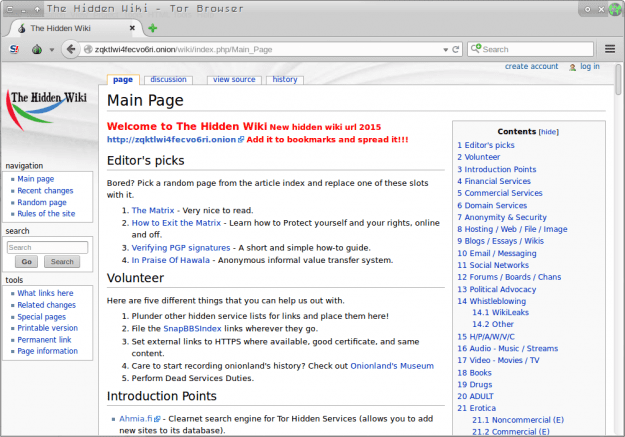
Keep in mind that this is not Google, but the Dark Web, so it will be difficult for you in finding your way around. This is exactly the reason why a Hidden Wiki exists. There are two versions of Hidden Wiki; one is a uncensored version, which will help you to access explicit content, or things that a righteous man would certainly condemn. As for the censored version, it will display the information as you can see in the image below.