Table Of Contents
Leet Botnet delivers 650 Gbps DDoS attack with junk packets made up of system files and embedded content
Mirai Botnet, the main culprit behind the massive Internet outage that hit East Coast and the Mid-West United States on 21st October has lost its DDoS crown to a new botnet called Leet Botnet. Up to now, the massive GBs required to power the DDoS attacks were due to millions of security cameras, routers and other Internet of Things connected devices which were infected with Mirai malware. Now researchers at DDoS mitigation service provider, Imperva have discovered a new botnet service called Leet Botnet which is capable of delivering DDoS attacks of 650 Gbps or more.
Read about the DDoS attack that took down America
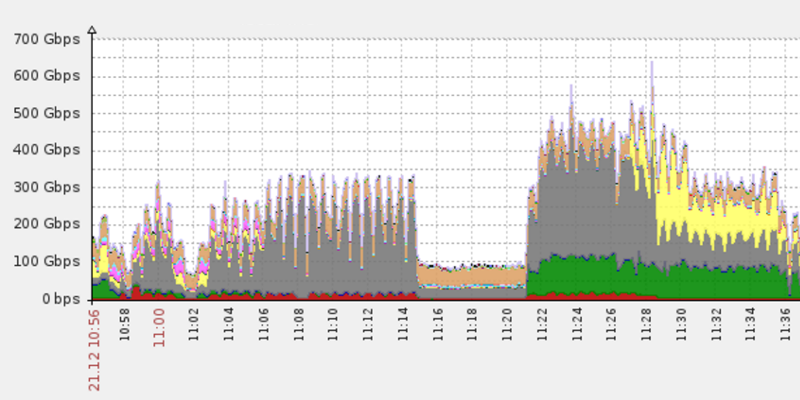
Imperva which helps websites protect against DDoS attacks, says it protected a client undergoing a DDoS attack of over 650 Gbps and over 150 million packets per seconds (Mpps) on December 21. The attack came in two different waves, both which attacked Imperva’s network after the attacker was unable to determine the target’s real IP address, which had been hidden behind the company’s mesh of proxy servers.
The first wave, as seen in the graphs above, peaked at 400 Gbps and lasted only 20 minutes. Seeing that the first flood barely made a dent, the attacker came back five minutes later with a larger DDoS cannon which fired junk packets of 650 Gbps on the Imperva network. Imperva says that that attacker tried to bring down its network for 17 minutes before realizing the futility called off his/her attack.
The Imperva crew named this unknown botnet as Leet because various TCP options in the junk traffic packets were arranged in such a way to spell out “1337,” which stands for “elite” in L33t speak.
Differences between Mirai botnet and Leet botnet
Researchers found three main differences in the way the two botnets differed. Mirai botnet is powered by a malware and infected Internet of Things devices and hence lack the technical capabilities to launch large SYN attacks while Leet Botnet seems to build just for doing that.
The second difference is that the DDoS attack packets via Mirai botnet were all hardcoded with several TCP options while Leet Botnet did not have those.
Lastly, Mirai botnet junk packets were made up of random-generated strings. For the Leet Botnet attack, the attackers had taken content from actual system files, embedded the content in the DDoS attack’s TCP packets, and sent it to flood the Imperva’s network.
Imperva researchers says that this is what led them to a conclusion that this DDoS attack was powered by a non-Mirai botnet and had the makings of a new botnet. Also, the Leet botnet wasn’t attributed to infected IoT devices and up to now no botnet made up of zombie desktop computers has been able to achieve such high GBs for a DDoS attacks.