Remember the Techworm post on Cryptolocker the Ransomware which locks your computer and demands Bitcoins in return for unlocking your computer. Well the Cryptolocker has been a high five success for its creators as per a study released by Dell SecureWorks CTU.
The Dell SecureWorks CTU has been making a indepth study into this malware since September 2013 when Cryptolocker was launched and its findings are very very shocking.
The Cryptolocker which completed 100 days since its release has managed to infect more then 200,000 to 250,000 systems world wide. The Cryptolocker was first spotted in the wild on 5th September 2013 and since then it has raised quite a storm in the ransomware business. Prior to Cryptolockers launch there where quite a few ransomware malwares such as Reveton, Urausy, Tobfy, and Kovter which have been successfull and cost many infected parties a lot of time and money but non have been above to achieve what Cryptolocker did in such a short span of time.
For the uninitiated, the ransomware prevents victims from using their computer normally (e.g., by locking the screen) and uses social engineering to convince victims that failing to follow the malware authors’ instructions will lead to real-world consequences. These consequences, such as owing a fine or facing arrest and prosecution, are presented as being the result of a fabricated indiscretion like pirating music or downloading illegal pornography. Victims of these traditional forms of ransomware like the ones given above could ignore the demands and use security software to unlock the system and remove the offending malware. However the entry of Cryptolocker changed the dynamics of ransomware. CryptoLocker changes this dynamic by aggressively encrypting files on the victim’s system and returning control of the files to the victim only after the ransom is paid. As pointed out in the earlier report on Techworm, the ransom is demanded in Bitcoins or from CashU/Ukash making it difficult to trace the ransom.
CryptoLocker manages to hide its presence from victims until it has successfully contacted a command and control (C2) server and encrypted the files located on connected drives. Prior to these actions, the malware ensures that it remains running on infected systems and that it persists across reboots. When first executed, the malware creates a copy of itself in either %AppData% or %LocalAppData%. CryptoLocker then deletes the original executable file.
CryptoLocker then creates an “autorun” registry key:
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun “CryptoLocker”:<random>.exe
Some versions of CryptoLocker create an additional registry entry:
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRunOnce “*CryptoLocker”:<random>.exe
The asterisk at the beginning of the key name ensures that the malware executes even if the system is restarted in “safe mode.”
Additional configuration data is stored in the following registry key:
HKCUSOFTWARECryptoLocker or HKCUSOFTWARECryptoLocker_0388
The VersionInfo value stored within this key contains configuration data encoded with the XOR key 0x819C33AE. The PublicKey value contains the RSA public key received from the C2 server during the initial network connection.
The executable files in early CryptoLocker samples used a random filename formatted like a GUID:
{71257279-042B-371D-A1D3-FBF8D2FADFFA}.exe
The vast array of file extensions are encrypted by Cryptolocker, few of the examples are given below :
| *.odt | *.ods | *.odp | *.odm | *.odb | *.doc | *.docx | *.docm |
| *.wps | *.xls | *.xlsx | *.xlsm | *.xlsb | *.xlk | *.ppt | *.pptx |
| *.pptm | *.mdb | *.accdb | *.pst | *.dwg | *.dxf | *.dxg | *.wpd |
| *.rtf | *.wb2 | *.mdf | *.dbf | *.psd | *.pdd | *.eps | *.ai |
| *.indd | *.cdr | ????????.jpg | ????????.jpe | img_*.jpg | *.dng | *.3fr | *.arw |
| *.srf | *.sr2 | *.bay | *.crw | *.cr2 | *.dcr | *.kdc | *.erf |
| *.mef | *.mrw | *.nef | *.nrw | *.orf | *.raf | *.raw | *.rwl |
| *.rw2 | *.r3d | *.ptx | *.pef | *.srw | *.x3f | *.der | *.cer |
| *.crt | *.pem | *.pfx | *.p12 | *.p7b | *.p7c | *.odc |
Each file is encrypted with a unique AES key, which in turn is encrypted with the RSA public key received from the C2 server. The encrypted key, a small amount of metadata, and the encrypted file contents are then written back to disk, replacing the original file. Encrypted files can only be recovered by obtaining the RSA private key held exclusively by the threat actors.
As a form of bookkeeping, the malware stores the location of every encrypted file in the Files subkey of the HKCUSOFTWARECryptoLocker (or CryptoLocker_0388) registry key. The Cryptolocker then gives the infected party specific time to get the keys to unlock their computers. Usually the encryption is so strong that the infected party normally pays. The Cryptolocker even has a system for late payment in case some infected party cant get to his/her system.
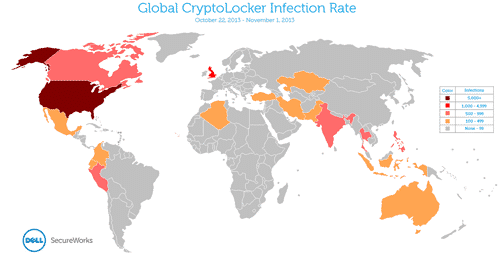
Judging by the way Cryptolocker operates, the whole system is elaborate with checks all the way till the infected computer contacts the Command Centre. And Cryptolocker has been very successful world wide as a RANSOMWARE for its creators as seen from below graph :
The United States was disproportionately represented among countries with measurable infection rates. Table 4 lists countries with the top ten infection rates.
| COUNTRY | NUMBER OF INFECTED SYSTEMS | PERCENTAGE OF TOTAL |
|---|---|---|
| United States | 22,360 | 70.2% |
| Great Britain | 1,767 | 5.5% |
| India | 818 | 2.6% |
| Thailand | 691 | 2.2% |
| Peru | 688 | 2.2% |
| Canada | 658 | 2.1% |
| Philippines | 645 | 2.0% |
| Indonesia | 427 | 1.3% |
| Iran | 333 | 1.0% |
| Ecuador | 264 | 0.8% |
As per the Dell SecureWorks, the makers of this malware have managed to earn somewhere around a eyepopping $30 to 35 million since its launch. It takes simple arithmetic to arrive at the sum. Cryptolocker takes some $300 as ransom per infected computer and going by conservative estimates if 200,000 computers have been infected, 200,000 x 300 comes to around $ 60,000,000 and tax free.
Authorities are yet to get any clue to where this malware originated or who has created it but it is a whopping success for its makers.
Source : Dell SecureWorks