A recent report by the Researchers at Kaspersky Lab have identified the fake “GOM Player Update” was responsible for the data theft at Japanese Nuclear plant (Monju fast-breeder reactor).
The Incident which took place earlier this year when one of the worker completed a update of “GOM player” which in fact was a fake update containing rogue Malware.
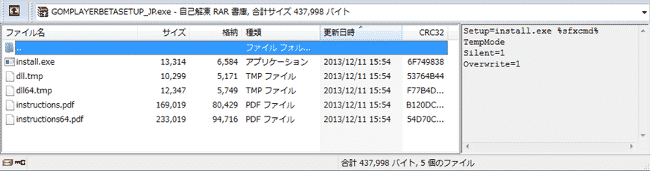
The Update file “GoMPLAYER_JPSETUP.EXE” which one executed unpacks itself and runs two Another Executable file with one being an legitimate update and Another one again unpacks 5 different file.
One of these files namely “Install.exe” was found to be Malicious in Nature and was detected as a Backdoor Named as “Backdoor.Win32.Miancha”
The investigation is still going on, and now it looks like the attack was not aimed to steal the data but most probably it was only the carelessness of an employ who unknowingly installed the Backdoor in one of the Computer at the Plant.