Table Of Contents
Stock Google Email App Version 4.2.2 for Android vulnerable to remote code execution : CVE-2015-1574
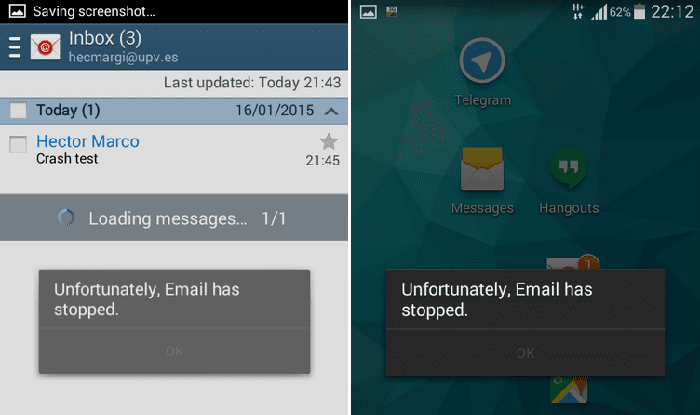
If you are using the stock Google Email App for Android on your smartphone you could probably be handing over the control of your smartphone to a potential hacker. Researchers Hector Marco and Ismael Ripol have discovered a vulnerability in the stock Google email app version 4.2.2.0200 which can allow potential hacker to remotely execute Denial of Service (DoS) attack with a specially crafted email.
In plain English this means that a specially crafted email sent to the App can crash the email App.
The vulnerability has been assigned CVE-2015-1574 and is deemed critical. “No interaction from the user is needed to produce the crash just receive the malicious email,” the researchers stated on HMarco blog.
The vulnerability
The bug appears because an incorrect handling of the Content-Disposition header by Google Email App. If an potential hacker sends a specially crafted email to the victim, the incorrect Content-Disposition header can cause the App to crash. The malformed header which causes the crash is :
Content-Disposition: ;
Whereas the correct Content-Disposition header should be :
Content-Disposition: attachment; filename=genome.jpeg;
So whenever the victim receives the malicious email, the application will crash while trying to download the email. The effect can be looping crash of the App, as every time the email App will attempt to open the email sent by hacker before the user can do anything. In effect, the App will be unusable till the offending email is removed by the user using other means like desktop email/Google Invite.
“Since the application crashes immediately, to remove the malicious email is a little bit tricky. The easiest and straightforward way to remove it is by using other email client (or via web) from the inbox at the email server. Another way is by disabling the internet connection (Airplane mode) before launching the email reader, and then you can remove the offending email,” the researchers stated on their blog.
The removal of the malicious email will however not prevent the hackers from sending similar mails and crashing the App again.
Proof of Concept (PoC)
To successfully exploit this vulnerability the attacker only needs to send an email to the victim with an empty Content-Disposition followed by a semicolon.
The researchers have written a simple python script which sends the crafted email to a target email user.
Email Android Google 4.2.2.0200 crasher
=======================================
Author: Hector Marco
Website: https://hmarco.org$ ./crash_Android_Google_email_4.2.2.0200.py -s [email protected] -r [email protected]
[+] Sending crafted message to: [email protected]
[+] Malicious email successfully sent.
The researchers stated that they tested the vulnerability on the App on Samsung Galaxy S4 Mini but have warned that this particular version is used by many smartphone users as default email App.
Fix
The researchers stated that the simplest fix is to update the App version to 4.2.2.0400 or higher.
However they added that updating is not possible in all cases.
For instance, current Samsung Galaxy 4 mini fully updated (17 Jan 2015) is vulnerable to this attack and not higher versions to 4.2.2.0200 are available after update the system from “Software updates,” the researchers stated.
Users using rooted Android smartphones can however bypass the official update channel and update their App. Another fix is to download the APK and install it on your smartphone.
You can access the PoC written by the researchers here (Python).