Internet providers like Airtel & MTNL are now intercepting your browsing data, and injecting it with additional ads & JavaScript code.
‘Water-boarding at Guantanamo Bay’ sounds like an adventurous weekend activity, to those who don’t have any idea about it.
Hopefully this post will help you to understand better — about what’s happening with you right now, without you even realising it.
Their goal? Is quiet simple is to earn additional revenue from us. Yes, additional revenue on the connections & services that we’ve already paid for!
To illustrate this with an analogy, it is like:
• Your car audio system inserting its own ads between songs you’re playing via your iPod.
• Your cell phone provider squeezing ad messages into your WhatsApp conversations with friends.
• Your phone calls being interrupted by an audio ad every hour.
• The pizza delivery guy swapping out one slice of your pizza with something you didn’t order.
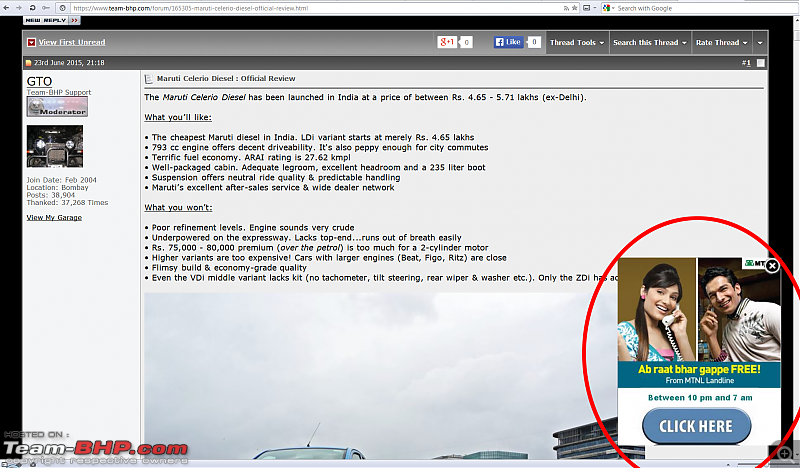
Here’s an example of what it looks like on MTNL. It’s not so easy to spot, since it only happens very occasionally:
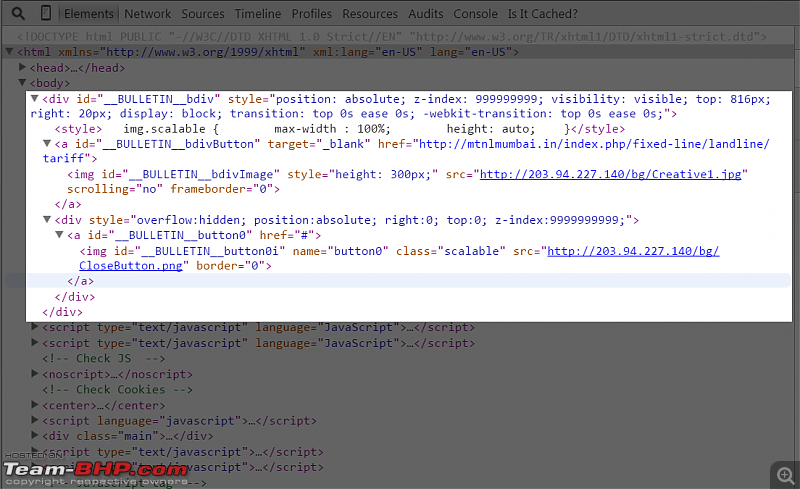
The highlighted code which you can see is NOT originally present on the Team-BHP webpage. Its MTNL, that has changed the contents of the page:
Dear Esteemed Customer, you might even get ads without a close button!
With new advertisers coming on board (eg. BankBazaar), you will no longer be able to easily identify these ads as the rogue ones from MTNL!
It gets worse! Soon they will be injecting:
• Animated ads: They are already experts in awful graphic design. This will just take it to the next level!
• Frames: Shifts the whole webpage to one side and inserts their ads beside it (or on both sides).
• Interstitials: Full-screen splash page ads before you are taken to your desired destination.
• Appear anywhere: Bad enough that they appear, but now they’ll appear anywhere on the page.
It’s also reported that:
• The maximum number of pop-up ads per device per day is restricted to 5.
• There seems to be no process in place to seek consumer consent before pushing ads into their browsing sessions.
Your Security is being Compromised:
• This is nothing short of a ‘Man In The Middle’ attack from our ISPs! (Definition = where the attacker secretly alters the communication between two parties who believe they are communicating directly with each other).
• The ISPs have the potential to do ANYTHING that a webpage can do – play audio, show an image, trigger a pop-up, redirect you to another site, attempt to access your webcam, record audio, etc. Imagine that.
• Unethical business practices draw all sorts of advertisers. Expect adware, malware & phishing to sneak through soon enough.
Time to say Bye-bye Privacy:
• These 3rd party partners have the ability to see what you’re browsing (even in private browsing mode).
• Ad networks love being nosy about user behaviour. Expect them to collect & sell data about your browsing habits too.
• Your landline phone number is used as an identifier for the ads. Combine this with the above point, and it’s a ridiculous breach of privacy (not to mention potential for tele-marketing).
Welcome Inconvenience:
• Slower page loads, since the content goes through an additional ad-server.
• Content on the websites you visit is covered by the rogue ads.
• The ads have a tiny close button that doesn’t even work correctly.
• They’ll use any possible invasive or irritating tactic to ensure you notice the ad.
Websites are the losers:
• The injected content covers ads from legitimate advertisers, blocking what the they have rightfully paid for.
• Most users will blame the website for having these awful ads, since they don’t realise it’s their shady ISP doing this!
Is it even Legal?
• Here’s what section 79 of India’s IT act has to say:
AIRTEL
A Few weeks back Airtel was also busted for injecting JavaScript code from an Israeli company Flash Networks into webpages:
Flash Networks then sent a ridiculous copyright infringement notice to the Bangalore techie who uncovered this malpractice.
Who is Flash Networks? Their LinkedIn page says:
Flash Networks is a global leader in optimization and monetization. Our solutions, enables operators to boost network speed, optimize video and web traffic, and generate over-the-top revenues from the mobile Internet.
Ironically, Airtel is expecting all its customers to be idiots, and claims the injected JavaScript is only to “track data usage”. Rubbish. There’s absolutely no need to inject JavaScript to do that.
HOW CAN WE STOP THIS?
We need to Raise Awareness:
• Most people don’t even realise this has been happening! Spread the word.
• Complain to the government via PGPortal
• Write an email to the MTNL abuse address – [email protected]
• If you run a website or blog, educate your visitors about the issue.
Most important; Protect Yourself:
• Use HttpS versions of sites, if available. (The encryption makes them harder to snoop on).
• Use a browser extension like Https Everywhere
• Use a VPN (secure connection to another ISP)
• Note: Simply blocking the ads is not a real solution. The ISP & ad network will still be able to see your browsing data.
• Note2: If there are any unsecured elements on the page, secure connections (https) can be compromised by these injections.
Get Social to educate everyone:
• Educate your friends. Click to share on : Facebook / Twitter / Google+ / LinkedIn
Resource : TeamBHP