New Vizio hack reveals company shares your data whether you accept its privacy policy or not
New research from Avast reveals just how easily compromised many so-called “smart” TVs actually are, as well as how little your consent to being tracked actually matters. It is apparent that Vizio’s Smart TVs track users’ viewing habits by default and this information is sold to third parties who can then use it to deliver targeted ads to other internet-connected devices that share an IP address or other identifier with the Smart TV). Avast researchers have found out that Vizio Smart TVs are also vulnerable to man-in-the-middle attacks that can result in attackers harvesting data that is sent from the TV to the server that collects it, as well as to attacks that could lead to attackers taking over control of the smart device and/or the entire home network.
Avast researchers tested Vizio’s Smart TV by hooking to a wireless access point on a test network, and took a look at the traffic going out and coming in. Among the various online services that the devices was sending requests to, was one (encrypted) to tvinteractive.tv.
This service is run by a service called Cognitive Networks, which identifies what the user is watching (via a “fingerprint”) and sends “an event trigger to the content provider or advertiser”, and they send back a link to the [Active Content Recognition] app to display onscreen.
Avast said that this communication is not secure because the TV doesn’t check the certificate of the HTTPS connection to control.tvinteractive.tv
“This means we can man-in-the-middle the connection, watch the requests, repeat them to the server, and serve our own fake (static) content back to the TV,” the researchers explained.
“As it turns out, the TV is not checking the certificate of the connection, but it is checking the checksum at the end of the data before it will use the data,” they shared. “We can serve this control data to the TV from our fake web server, but we cannot change the data without breaking the checksum. The checksum is md5, and we assume the control data is combined with a secret to generate the checksum. In the field of cryptography this type of secret key is referred to as ‘salt’.”
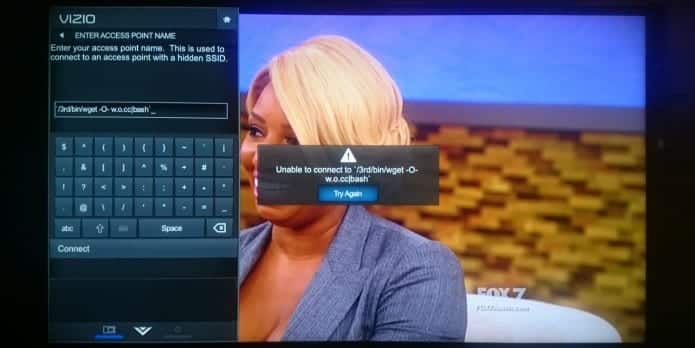
Unable to brute-force it, the researchers wanted to see if they can get the salt from the device. They forced their way in via a local command injection into a screen for configuring a hidden wireless network ID, found a way to list the commands, “owned” the TV, and found the salt. This allowed them to use a checksum that will make the sent data be accepted by the TV.
“At this point, we have a possible attack vector into the home network or office through the Smart TV, which can be accomplished by hijacking DNS and serving malicious control data to the TV. Because the TV calls out to a control server by default and does not verify the authenticity of the control server, it allows an attacker in without the need for any incoming ports to be opened,” they concluded.
After Avast researchers discovered these holes they notified Vizio which promptly issued patches for the flaws. The update with the patch will be pushed to all the devices in the next few days, and those TVs who have automatic updating on and are online will update themselves.