Cyber criminals extorting money from Android Smart TV owners after encrypting their TVs with ransomware
Looks like whatever the security firms do to catch up with them, the cyber criminals manage to go one step head. Amidst ransomware threats making headlines in past few weeks a new type of threat has emerged.
When one just thought that cybercriminals were only interested in hacking websites, stealing passwords, etc., it looks like they have moved on to a new field of interest, which is Internet of Things (IoT). In other words, if you own a Smartwatch, Smart TV, Smart fridge, or any Internet-connected smart device, you may want to be careful.
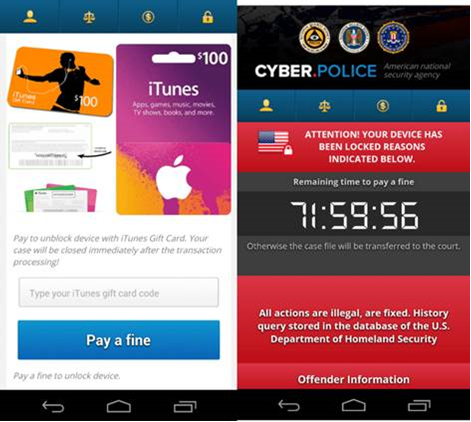
Trend Micro researchers have come across an Android mobile lock-screen ransomware, known as ‘FLocker’, which is capable of locking Android smartphones as well as Smart TVs. Yes, you have heard it right!
Echo Duan, a Trend Micro researcher wrote in a blog post that ever since FLocker (detected as ANDROIDOS_FLOCKER.A and short for “Frantic Locker”) version came out in May 2015, more than 7,000 variations of the malicious ransomware have been traced by the company. The FLocker ransomware initially targeted Android smartphones with its developers continuously updating the ransomware and adding support for new Android system changes.
“This is the first major instance of ransomware to infect TVs that we’ve found,” Christopher Budd, global threat communications manager, told SCMagazine.com in an email.
According to the report, its author kept rewriting the malware to prevent detection and enhance its routine. “Over the past few months, we have seen spikes and drops in the number of iterations released. The latest spike came in mid-April with over 1,200 variants,” said the company.
This FLocker operates as a police Trojan and attempts to scare the potential victim into paying by claiming to be the US Cyber Police or another law enforcement agency. Once the malware is downloaded and the TV locked, the hacker accuses potential victims of crime they didn’t commit and demands $200 in iTunes gift cards to have the Smart TV or mobile device unlocked.
Ironically, the very convenience the owners obtain by using multiple devices that run on one platform makes life easier for the hackers. “Using multiple devices that run on one platform makes life easier for a lot of people. However, if a malware affects one of these devices, the said malware may eventually affect the others, too,” Duan wrote.
“As far as how, it’s being delivered through standard infection vectors: nothing new or special. The TVs in this case are accidental collateral damage of the ransomware, and not specifically targeted. They just happen to be running an attackable version of Android.” Budd said.
There is little difference between FLocker that attacks mobile devices and the version that goes after Smart TVs.
“To avoid static analysis, FLocker hides its code in raw data files inside the “assets” folder. The file it creates is named “form.html” and looks like a normal file. By doing so, the code of “classes.dex” becomes quite simple and no malicious behavior could be found there. Thus the malware has the chance to escape from static code analysis. When the malware runs, it decrypts “form.html” and executes the malicious code,” he wrote.
Trend Micro says the malware is configured to deactivate itself in some regions including Russia, Bulgaria, Hungary, Ukraine, Georgia, Kazakhstan, Azerbaijan, Armenia, and Belarus.
However, if FLocker detects devices outside these countries, the malware will wait for 30 minutes. After the short waiting period, it starts the background service which requests device admin privileges immediately. If the user denies the request, it will freeze the screen faking a system update.
FLocker runs in the background and connects to a command and control (C&C). The C&C then delivers a new payload misspelled.apk and the “ransom” HTML file with a JavaScript (JS) interface enabled. This HTML page has the ability to start the APK installation, take photos of the affected user using the JS interface, and display the photos taken in the ransom page.
The ransom webpage fits the screen, irrespective if it infected a mobile device or a smart TV.
Even though the new variant of FLocker does not encrypt files on the infected device, it has the capability of stealing data from the device, including contacts, the phone number, device information and location data.
While Trend Micro’s report is not clear as to how FLocker infects smart TVs, it does mention that typically ransomware infection arrives via SMSes or malicious links.
Therefore, you should be cautious while browsing the Internet, and receiving text messages or emails from unknown sources.
For those people who do not reside in Eastern Europe Duan recommended on his blog, “We suggest user to contact the device vendor for solution first if their Android TV gets infected.”
For those victims who are a little tech savvy, they can possibly handle the task on their own. He said, “Another way of removing the malware is possible if the user can enable ADB debugging. Users can connect their device with a PC and launch the ADB shell and execute the command “PM clear %pkg%”. This kills the ransomware process and unlocks the screen. Users can then deactivate the device admin privilege granted to the application and uninstall the app.”
He further added, “For securing mobile devices, we advise installing security software in their smart devices to protect it from malicious apps and threats. Trend Micro Mobile Security and Trend Micro Mobile Security Personal Edition protects users from this ransomware and other related threats. Trend Micro Mobile Security Personal Edition is available on Google Play.”
Next time your Android smart TV refuses to play, you should know your are in for a big ransom.


