Table Of Contents
Learn How To Crack Android Full Disk Encryption
When it comes to encryption of personal and sensitive data on Android smartphones and tablets, Android users are always at severe risk, as a security researcher has shown how Android’s full-disk encryption can be cracked much more easily than expected with brute force attack and some patience.
Starting with version 5.0, Google started to implement Full Disk Encryption on Android. The thought behind this security feature is to prevent both hackers and even powerful law enforcement agencies from gaining unauthorized access to device’s data.
The recent heated battle between Apple and the FBI case proved that full disk encryption can protect data even from powerful organizations. Even though the FBI managed to gain access to the data later, it had to end up hacking the device instead of beating its full disk encryption implementation.
In short, Android’s disk encryption is the process of encoding all user’s data on an Android device before ever written to disk using user’s authentication code. The disk is decrypted only when the Android user enters his/her password.
All of this takes place in the background and is not visible to the user. To enhance the security of the data, Google implemented additional means such as delays between password attempts to make brute forcing less useful, and also an option to wipe the data after failed decryption attempts.
Recently, a security researcher examined Android’s full disk encryption implementation and came to the conclusion that the feature is not as secure as the company claims it is, and he has a working code to prove it.
Cracking Android Full Disk Encryption : Security researcher releases Extract Key Master Online
Security researcher Gal Beniamini has found severe problems (CVE-2015-6639 and CVE-2016-2431) in how Android devices handle its full disk encryption, making it very easy for hackers to get access to the user’s sensitive data. In other words, Android’s disk encryption on devices with Qualcomm chips is based only on your password.
By abusing two security vulnerabilities discovered in 2014, the researcher was able to gain code execution privileges within the TrustZone kernel. Qualcomm did create patches for these vulnerabilities.
While you may think that this is the case anyway, in reality, Android uses your password to create a strong 2048-bit RSA key (KeyMaster) derived from it instead.
Another carryout from the analysis is that Qualcomm or OEMs can comply with government or law enforcement agencies to break the FDE.
Qualcomm runs in the Snapdragon TrustZone to protect serious functions like encryption and biometric scanning, but Beniamini discovered that it is possible to exploit an Android security flaw to extract the keys from TrustZone.
“Since the key is available to TrustZone, Qualcomm, and OEMs [Original Equipment Manufacturers] could simply create and sign a TrustZone image which extracts the KeyMaster keys and flash it to the target device,” Beniamini wrote. “This would allow law enforcement to easily brute force the FDE password off the device using the leaked keys.”
This means that an attacker could perform a brute-force attack to seize the user password, PIN or lock, cracking Android’s full disk encryption once it gets hold of this key.
Again, restructuring the attack involves executing code within the TrustZone kernel, which means that creating a modified TrustZone kernel image is not enough.
In the end, it means that when Qualcomm chips are used, the hackers can break Android’s full disk encryption, and OEMs or Qualcomm may be compelled to do the same.
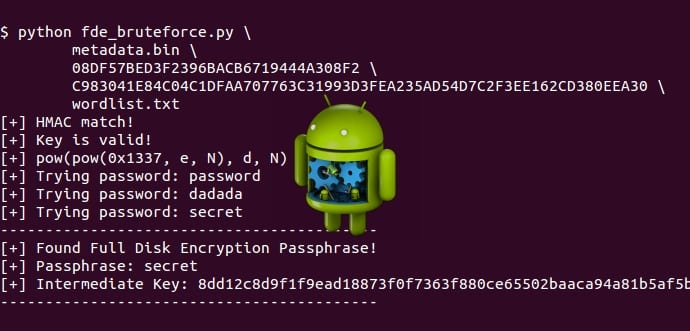
Beniamini has published a detailed step-by-step guide this week on how one can break down the encryption protections on Android smartphones powered by Qualcomm Snapdragon processors, and a brute force script to brute force Android’s full disk encryption off the device.
You can find the full source of the exploit, Extract Key Master on GitHub.
Source: Ghacks