Table Of Contents
Kim Jong-un’s homebred Linux distro for North Korea, RedStar Linux vulnerable to remote takeover
If you have read our year old article, you will know that the despotic North Korean regime led by Kim Jong-un last year decreed that all the North Korean computers should run on Linux based RedStar operating system. This was Jong-un’s way of saying to the United States that we don’t need your Microsofts and Apples on our computers. But it so happens that Kim Jong-un’s homebred operating system has a serious vulnerability that lets any hacker get root access.
Researchers at HackerHouse have discovered a vulnerability in Naenara, the Firefox-based web browser of North Korea’s home-grown operating system. The Red Star OS, having trivial remote exploit attack vectors, seems to aggravate security issues concerning North Korea Government.
While it is obvious that the main aim of deploying this OS was to interfere with privacy of the citizen and to spy on them, it is also clear now that North Korea has accidentally given this “right” to almost every hacker in the world.
Remote Code Execution is a vulnerability that when exploited , lets the attacker execute arbitrary code on victim machine remotely(over the intranet or the Internet). Obviously, this was not an expected “feature” of this OS.
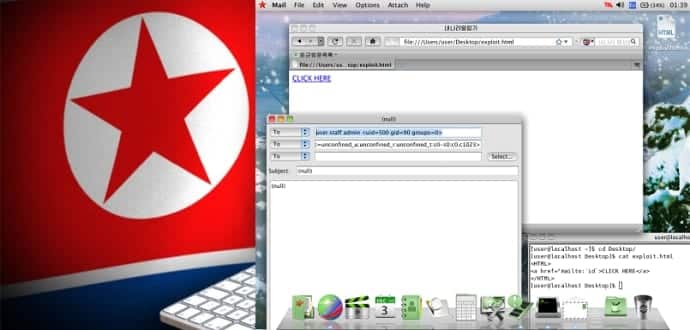
The exploit according to HackerHouse works like this:
Registered URL handlers are passed to a command-line utility “/usr/bin/nnrurlshow”. This application (aside from having null ptr de-refs and other cute bugs) takes URI arguments for registered URI handlers when handling application requests such as “mailto” and “cal”. Naenara doesn’t sanitize the command line when handling these URI argument requests and as such one can trivially obtain code execution by passing malformed links to the nnrurlshow binary. An attacker can get a user of RedStar OS 3.0 to execute arbitrary commands by enticing them to click on a link which points to “mailto:`cmd`”. Commands will then be executed as arguments when passed to evolution mail.
In simpler words:
The arguments passed in URI’s are not being properly handled for malicious input, it lets an attacker place some command line code as an argument in a URI , from a document which contains a hyperlink having this URI and send it to the victim. Once the victim clicks the link, all those commands are executed on victim’s system.
What to expect next?
This vulnerability is not going to be fixed as soon as it should be, leaving severe potential impacts on North Korean people’s data and other digital assets. It is always advisable to go with the well known operating systems to maintain everything in place. For enthusiasts, a link to images of Red Star OS is provided.
More details, original documentation, and images of Linux based RedStar OS can be found here.