Table Of Contents
Smartphone unlock patterns can be hacked using SonarSnoop attack
Researchers from Lancaster and Linkoping University have come up with a new attack technique that uses your smartphone’s speaker and microphone to steal unlock patterns from Android devices, reports ZDNet.
Dubbed as ‘SonarSnoop’, this method transforms a smartphone’s speaker and microphone into a sonar and uses sound waves to track a user’s finger position across the screen. In other words, the attack technique depends on the basic echo principle of sonar systems.
Also Read- Android smartphones can be hacked with AT commands attacks
For those unaware, Sonar (Sound Navigation and Ranging) uses sound propagation normally in submarines for detecting objects on or under the surface of the water, such as other vessels.
The study has been published in the research paper titled “SonarSnoop: Active Acoustic Side-Channel Attacks” that has detailed testing information of SonarSnoop on a Samsung Galaxy S4 running Android 5.0.1.
How does the SonarSnoop attack work?
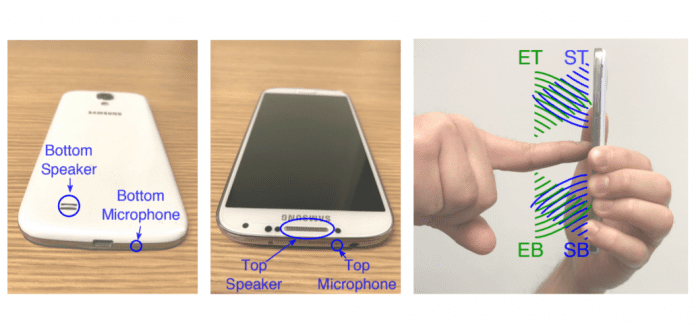
SonarSnoop uses FingerIO as the primary source of inspiration and is the malicious version of FingerIO. The attack uses a malicious app on the device that emits sound waves from the phone’s speakers generated at frequencies – 18 KHz to 20 KHz – that are inaudible to the human ear.
The malicious app uses the device’s microphone to pick up the sound waves and bounces it back to nearby objects, which in this case are the user’s fingerprints. Depending on the position of the speakers and microphones, a machine learning (ML) algorithm is employed in the malicious application to determine the possible unlock patterns.
“The received signals are represented by a so-called echo profile matrix which visualizes this shift and allows us to observe movement. Combining observed movement from multiple microphones allows us to estimate strokes and inflections,” the researchers explained.
Results of SonarSnoop attack
With the help of SonarSnoop, the researchers were able to reduce the number of possible unlock patterns by more than 70%. Thanks to the ML algorithms built into the attack. The research team used 12 unlock patterns with 15 unique strokes in their experiment.
SonarSnoop currently cannot unlock the devices with 100% accuracy, as the method is still in the experimental stage. However, the accuracy is expected to improve with the ML Algorithm becoming more efficient with time, thereby reducing false unlock patterns.
Researchers also point out that although their experiment focuses on smartphones, SonarSnoop is “is applicable to many other kinds of computing devices and physical environments where microphones and speakers are available.”
Also Read- Hackers can spy on your computer screens through the webcam microphone