A group of security researchers have discovered a new method to hack smartphone voice assistants, including those used by Siri and Google by sending voice commands via ultrasonic waves.
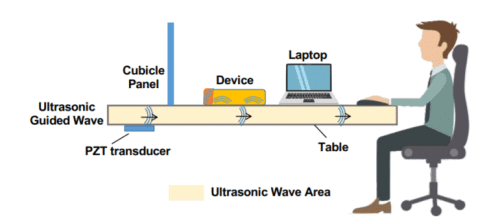
Dubbed as SurfingAttack, this attack allows a hacker to control Apple’s Siri and Google Assistant by sending inaudible vibrations through a tabletop from 30 feet away without the phone owner’s knowledge.
The research was carried out by a group of academics from Michigan State University, the University of Nebraska-Lincoln, Washington University in St. Louis and the Chinese Academy of Sciences.
In their paper, SurfingAttack: Interactive Hidden Attack on Voice Assistants Using Ultrasonic Guided Waves, the researchers have demonstrated how smartphone voice assistants can be exploited through solid objects, such as metal, glass or wood table using ultrasonic waves.
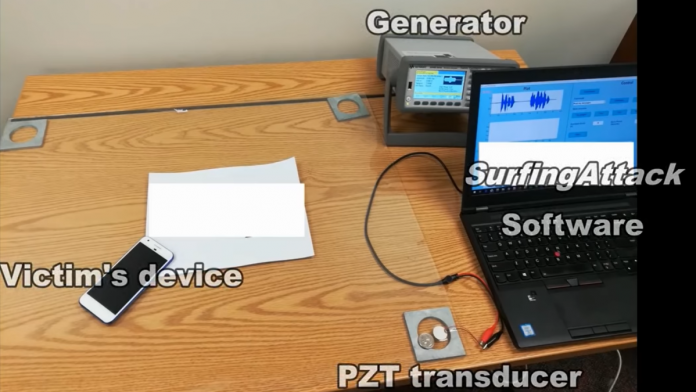
Basically, SurfingAttack modulates the voice command onto the inaudible frequency band and transmits attack signals using an off-the-shelf PZT transducer (cost $5 per piece) through different types of tables made of solid materials.
The researchers tested their SurfingAttack technique on 17 models from Apple, Google, Samsung, Motorola, Xiaomi, and Huawei. Of these,13 models were running Android with Google Assistant, and four iPhones had Apple’s Siri.
The researchers were able to successfully take control of 15 of the 17 smartphones. However, the technique was ineffective against Huawei’s Mate 9 and Samsung’s Galaxy Note 10+, as the construction material of these phones “dampened the ultrasonic waves.”
They were able to successfully activate the voice assistants, command them to unlock devices, hijack SMS two-factor authentication codes, take repeated selfies, and even make them place fraudulent calls.
To hide the attack from the victim, the researchers turned down the concealed microphone’s volume to make the voice responses unnoticeable.
“By leveraging the unique properties of acoustic transmission in solid materials, we design a new attack called SurfingAttack that would enable multiple rounds of interactions between the voice-controlled device and the attacker over a longer distance,” the researchers said on their website.
“SurfingAttack enables new attack scenarios, such as hijacking a mobile Short Message Service (SMS) passcode, making ghost fraud calls without owners’ knowledge, etc.”
“We want to raise awareness of such a threat,” said Ning Zhang, an assistant professor of computer science and engineering at St Louis. “I want everybody in the public to know this.”
Researchers suggest the following measures to defend yourself against SurfingAttack:
- Keep an eye on your devices placed on tabletops.
- Reduce the touching surface area of your phones with the table.
- Place the device on a soft woven fabric before touching the tabletops.
- Use thicker phone cases made of uncommon materials such as wood.
- Turn off lock screen personal results (or unlock with voice match) on Android.
- Disable your Voice Assistant on the lock screen, and lock your device when you put it down.
The results were presented at the Network and Distributed Systems Security Symposium in San Diego, California on February 24, and also subsequently published a summary on the university website.