As the tech firms, security firms and authorities tighten their security, the cyber criminals develop new and more hideous ways to make money and stay two steps ahead of the security guys. The latest malware discovered by Symantec is called ‘Ploutus’ and it can make a ATM spew out cash through text message directions sent from a remote command and control server.
Symantec which has been tracking this malware says that the Ploutus first appeared in Mexico. The author of this malware has written it in such a way, that it is intended to exploit and hack only certain types of stand alone ATMs. Symantec has not yet been able to identify the type of exploit the author uses or the type of ATM which is hacked but it has obtained one of the ATMs used in this kind of attack. Symantec is now studying how Ploutus works, but as of now pending investigation, it has not disclosed the brand name of the ATM manufacturer.
Symantec has stated that the cyber criminals are targeting standalone ATMs because the malware has to be planted on machine. For doing this, the cybercriminals need physical access to the ATM which they plan to hack and only standalone ATMs with little security allow that.
Symantec says that the latest version of the Ploutus named Backdoor.Ploutus.B is more dangerous than the earlier version of Ploutus. The earlier Ploutus allowed it to be controlled via the numerical interface on an ATM or by an attached keyboard. But Backdoor.Ploutus.B allows the author or the malware owner to remotely control the ATM via a text message.
 |
| Infographic courtesy Symantec |
As seen in the image (courtesy Symantec), the attackers target a standalone ATM, infiltrate and infect it with a Ploutus trojan which is connected to a mobile phone via USB port and then use this mobile phone as a controller. Once the entire setup is in place, the attacker can send SMS commands like withdrawal via text messages to the ATM and a accomplice of the attacker can physically collect the cash.
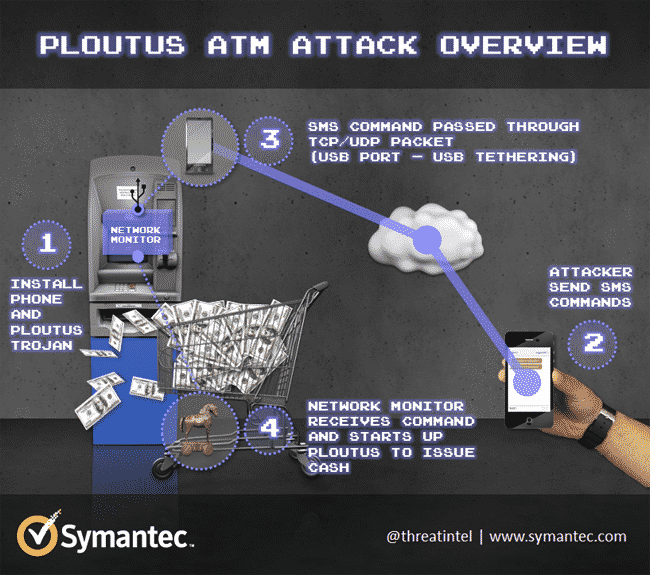 |
| Infographic courtesy Symantec |
“When the phone detects a new message under the required format, the mobile device will convert the message into a network packet and will forward it to the ATM through the USB cable,” wrote Daniel Regalado, a Symantec malware analyst. He also added that Ploutus has capability to monitor all incoming traffic to the ATM via a network packet monitor. When it detects a valid TCP or UDP packet from the phone, the module searches “for the number “5449610000583686 at a specific offset within the packet in order to process the whole package of data,” he added.
It then reads the next 16 digits and uses that to generate a command line to control Ploutus. Once this command line has been compromised, the ATM is at the disposal of the cyber criminals. Symantec also added that the impending withdrawal of support for Windows XP run ATMs may also result in easy pickings for the author/attackers of Ploutus.
“The master criminal knows exactly how much the money mule will be getting,” The banks having standalone ATMs in their inventory have a lot to think about. You can see the following video from Symantec detailing the use of Ploutus
Resource : Symantec
