In a blog post Researcher Chaman Thapa explained that the Facebook lets users embed various HTML tags into their notes which can be exploited to launch a DDoS website on any website.
Facebook Notes allows users to include <img> tags. Whenever a <img> tag is used, Facebook crawls the image from the external server and caches it. Facebook will only cache the image once however using random get parameters the cache can be by-passed and the feature can be abused to cause a huge HTTP GET flood. Thapa said in blog.
Lets Suppose a attacker want to DDoS a website targetx.com that have a image or a PDF file on its server, he will just replace the link with the file link and use it multiple times.
<img src=https://targetname/file?r=1></img>
<img src=https://targetname/file?r=1></img>
..
<img src=https://targetname/file?r=1000></img>
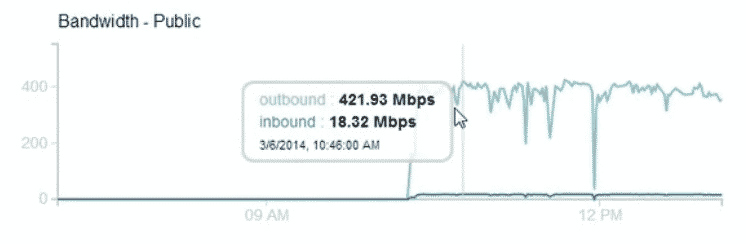
Thapa Demonstrated his concept over a target using 3 laptop and the only browser he was able to achieve 400+ Mbps outbound traffic for 2-3 hours using a Image file.
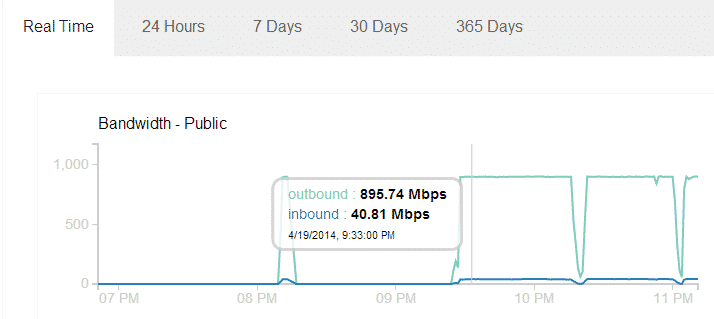 In one other Demonstration Thapa was able to launch a 900+Mbps Outbound traffic using a 13 mb Pdf file. which was fetched by Facebook 180,000+ times and the number of Facebook servers used were 112.
In one other Demonstration Thapa was able to launch a 900+Mbps Outbound traffic using a 13 mb Pdf file. which was fetched by Facebook 180,000+ times and the number of Facebook servers used were 112.Think about a situation when multiple users are trying to access the note at a similar time, the amount of Inbound traffic can be extended to a much higher level resulting in a very strong DDoS attack which is strong enough to bring down any average website.
Unfortunately Facebook has no plan to fix the vulnerability, In the end, the conclusion is that there’s no real way to us fix this that would stop “attacks” against small consumer grade sites without also significantly degrading the overall functionality. Facebook replied to the researcher.