More than half a million United States Dollars were siphoned of using a banking Malware. The banking malware fraud campaign which has siphoned more than half a million dollars from a European bank over the course of a week from 10th to 20th Jan, 2014 from 190 victims was discovered by researchers at Kaspersky Lab. In a report posted on Secure List blog says that researchers at Kaspersky Security have discovered this fraud campaign, which they have dubbed ‘Luuuk’ siphoned of exactly €500,000.00 ($679,700.00) from 190 victims from a European Bank. The victims were mostly from Italy and Turkey, the post said.
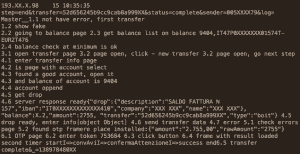
Luuuk was detected by Kaspersky researchers when they chanced upon suspicious looking control and command server. The server contained multiple log files that showed bots conversing with a Web panel. The data extracted by Kaspersky suggested a financial fraud because it included victims’ details such as the amount of money stolen from clients’ bank accounts.
The Kaspersky researchers named the fraud after the panel used in the server which was /server/adm/luuuk/ Kapersky said that the scam was executed through a combination of man-in-the-browser attacks that allowed the criminals to usurp victims’ credentials via a Web injection. After the money was siphoned of it was then routed to a automatic “pre-set money mule accounts” which Kaspersky believes belongs to the cyber criminals or their couriers. According to GReAT’s research, there were four separate drop groups that transmitted funds via special bank accounts and via cash-outs at ATMs.
One particular group was responsible for transferring sums of €40,000 to €50,000 , another was responsible for transferring 15,000 to 20,000 Euros, and a third was responsible for transferring between €2,500 and €3,000. The last drop group was responsible for transferring between €1,750 and €2,000.
“The Luuuk’s bosses may be trying to hedge against these losses by setting up different groups with different levels of trust: the more money a ‘drop’ is asked to handle, the more he is trusted,” said Vicente Diaz, a principal security researcher with GReAT.
As of now it is unclear as to exactly which malware was used for this fraud but experts believe that it may be a strain of Zeus or a freshly authored malware that allows the interception of financial data automatically, as soon as users log into their bank accounts. There is a strong possibility that a strain of Zeus was used as Zeus is know to have plenty of variations like Citadel, SpyEye and IceIX. All the above variations have almost similar configurations as was used by the cyber criminals in this case.
While Kaspersky has notified the concerned bank and investigating agencies, the Command & Control server associated with Luuuk disappeared two days after it was discovered which indicates that the authors/owners of Luuuk may have been alerted about its discovery. Some experts believe that Luuuk is not dead and may arise again in some remote part of the world to siphon money from some other banks.
“Based on the transaction activity we believe that this could be an infrastructure change rather than a complete shutdown of the operation,”