A rare Android work which spread itself through Android mobile phones has sprung up in the wild. Security researchers at AdaptiveMobile have discovered this Android malware which is dubbed Selfmite. It propagates via SMS text messages and send links to sends malicious links to 20 contacts present in the device owner’s address book.
SMS worms are not a common occurence, A few months before the discovery of Selfmite, In April experts at ESET discovered a malware targeting Russian-speaking Android users, dubbed Samsapo, which abuses a person’s contact list to propagate itself to other devices.
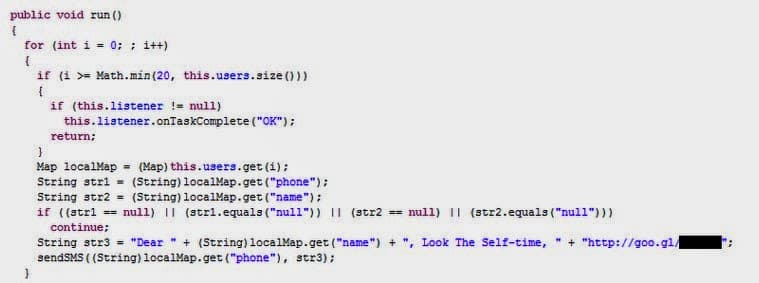
Coming back to the Selfmite. Selfmite worm once infected in your Android smart phone, sends a SMS messages to 20 contacts from your address book. The components of the message are given below :
“Dear [NAME], Look the Self-time,” followed by a shortened URL generated with goo.gl.
The Google generated link shortner is in fact a malicious link points to an APK file called TheSelfTimerV1.apk. Once the victim downloads and installs the APK, it will appear as a SelfTimer icon on your mobile screen. If the victim launches it, the malware will immediately read device’s contact book for a name + phone pair and send 1 message to 20 different contacts using the name as a greeting. The following code is executed to send the messages to your contacts.
After sending malicious SMS messages to the new potential victims, the Selfmite worm will open https://173.244.***.***/message.php URL in the web browser and try to access another goo.gl URL stored on this web page. The shortened URL will be resolved to https://apx.rdkt.avazutracking.net/iclk/redirect.php?apxcode=[REDACTED]&id=[REDACTED] and further to https://seth.a2.avazutracking.net/tracking/redirect/redirect.php?id=[REDACTED]&czid=[REDACTED]=&usrid=[REDACTED]&rgid=[REDACTED]&kw=[REDACTED]&vurl=[REDACTED]. After this the user will be offered to download and install a mobogenie_122141003.apk file.
The Selfmite worm to convinces users to download and install a file called mobogenie_122141003.apk. Mobogenie is a App which allows Android users to synchronize their devices with PCs and download Apps from an alternative app store. Though Mobogenie is legal, there are lot of java executeable ads on websites which download Mobogenie Market App without owners permission which the owner is surfing on a website with such a ad code.
“As you might have already noticed Selfmite worm uses advertising platform to redirect user to the particular version of Mobogenie app. And this particular version of Mobogenie app will ‘click’ after the installation to a certain URL with additional device parameters in order to confirm the Mobogenie app installation. So as a result we believe that an unknown registered advertising platform user abused legal service and decided to increase the number of Mobogenie app installations using malicious software.” is reported by AdaptiveMobile in the blog post.
Experts at AdaptiveMobile have already detected dozens of devices infected with Selfmite in North America, the malicious short goo.gl URL used to spread the malicious APK was visited 2,140 times until Google disabled it.
If you happen to download Mobogenie through this trick or any executable ad network, do go to downloads and delete it. Also remember to Settings > Security > and click on Verify apps. Also unclick Unknown sources. This will not allow your Android smart phone to automatically install the malicious Apps like above.