A new of Ransomware called Critoni is being sold on on the underground forums. The speciality of this ransomware is that it uses the Tor network to communicate with the remote command and control server. This anonymizes the communication and hence makes it undetectable as the ransomware commands go through the several layers of Tor anonymiser setup before reaching the Command and Control server.
For the uninitiated, a Ransomware is a malware that once infected in your computer, encrypts various types of files, documents, videos and images with a encrypted key and then asks you to pay ransom for the keys to decrypt your data.
The post offering the sale of Critoni was discovered by French security researcher. Kafeine, who says that the advertisement has been up since the middle of June 2014. He said the going price for this malware is $3,000.00/ €2,220.00 / Rs.180,000.00.
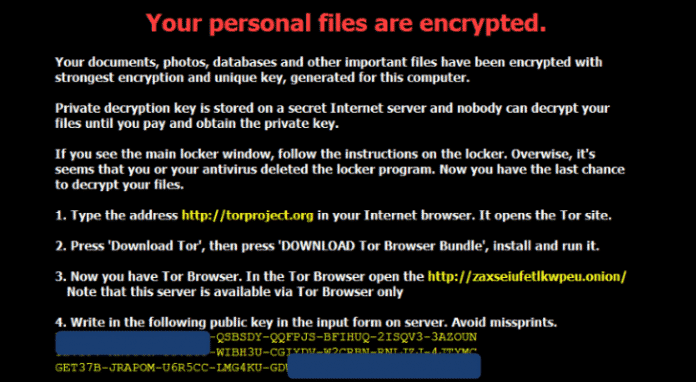
This particular malware is named CTB-Locker (Curve-Tor-Bitcoin Locker) by the cyber criminals and named Critoni.A by Microsoft. Critoni uses persistent cryptography relying on elliptic curves, which would make file decryption impossible; keys are generated randomly and there is no risk of two keys being same. If infected the ransom has to be paid in bitcoins in order to prevent tracing of the transaction. The ransomware also gives a tutorial about how to obtain bitcoins through market if he/she doent own any. In fact, if the victim are new to Tor Anonymizer Network, it even gives tutorials about downloading the Tor.
According to Kafeine, the post on the underground forum also mentioned that the encryption process could be carried out in lack of Internet connection, but how it could connect with its C & C server in that case is a question. Kafeine also reports that Critoni has been seen to be delivered by the Angler exploit kit, but other forms of attack have also been detected in the wild.
Another attribute of Critoni is that once the period of time set for making the ransom payment expires, the file locking program automatically self-deletes itself and victims are offered another chance to retrieve the data. These instructions are provided in a TXT file located in the Documents folder.
According to security experts from Kaspersky, this is the first cryptomalware to use the Tor network to annonymize its communication with the command and control server. This sort of protection has generally been seen in banking Trojans like Zues malware.
In a report on Threatpost, Fedor Sinitsyn of Kaspersky said, “Executable code for establishing Tor connection is embedded in the malware’s body. Previously the malware of this type, this was usually accomplished with a Tor.exe file. Embedding Tor functions in the malware’s body is a more difficult task from the programming point of view, but it has some profits, because it helps to avoid detection, and it is more efficient in general.”
Using Tor network reduces the risk of detection and make it easier for the cyber criminals to mint bitcoins through hapless victims of Critoni.A