The software known as Semalt, which claims to be an ‘SEO tool,’ has been found to be using Soundfrost malware to hijack hundreds of thousands of computers. In the last 30 days, it has organized a huge spambot that is originating from more than 290,000 different IP addresses around the globe, with a concentration in South America.
“Its unscrupulous behavior already having caused concern to many website owners, in what appears to be a large-scale, referrer spam campaign, Semalt is most commonly accused of ignoring ‘robots.txt’ directives and overbearing servers with a slew of suspicious-looking requests,” said Incapsula researcher Ofer Gayer, in a blog.
Perhaps unsurprisingly given the level of infection, its spamming reach is quite prodigious already: In all, Incapsula found that Semalt bots have attempted to spam 32% of all websites on its service.
Semalt is pushing out referrer spam, which belongs to a niche within the spamming ecosystem. In Google’s search algorithm, the more links that point to a website, the further up in the search results it will be. In other words, a, dog grooming page that has 100 links pointing to it from other sites will be presented above competing dog grooming sites that may have just one or two of these referral links.
Semalt is essentially creating bogus referral links to fool Google’s algorithm into thinking a site is more popular than it actually is.
“Somewhere between Facebook clickjacking campaigns and 419 scams, referrer spam lays a scheme to improve search engine rankings by relying on bad practices adopted by naïve, unsuspecting webmasters,” explained Gayer.
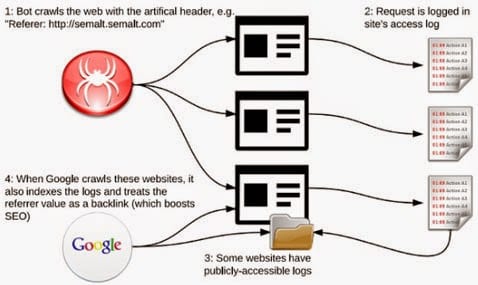
The perpetrators create the phony links to a certain URL by abusing publicly-available access logs. Typically they use crawl bots to locate vulnerable websites, often accessing hundreds of thousands of websites in bulk, and then they send out requests from there with a synthetically-generated ‘referrer’ header. Each of these headers contains the website URL the perpetrators are trying to boost.
All such requests are automatically recorded in access logs, creating an HTML referrer link. These links are then crawled by search engines. Because of an unusual ability to execute JavaScript, Semalt activity actually appears in Google Analytics reports as being ‘human’ traffic.
This process works well until Google or another search engine figures out that it’s a scam—thus impacting unsuspecting websites that have been hijacked.
“The existence of such SEO leeches can cause long-term SEO damage to websites, ranging from demotion in search engine result pages (SERP) to complete SERP blacklisting and removal,” said Gayer. “Technically speaking, this activity does not pose a security threat, nor does it have any visible side effects. As a result, referrer spam may go unnoticed by many website owners.”
Also, in Semalt’s case, it isn’t running a regular crawler to uncover vulnerable websites; instead, it appears to use a botnet generated by malware hidden in a utility called Soundfrost and includes machines on over 290,000 different IP addresses around the world. Nearly 60 percent of those machines are located in Brazil.—which could be behind several other malicious activities.
“Beyond providing Semalt with the scale it needs to operate, this botnet also helps Semalt’s bots avoid rudimentary security practices such as IP blacklisting and rate-limiting,” Gayer said. “This, coupled with its ability to overcome challenge-based bot detection mechanisms, makes Semalt’s shady activity that much more concerning.”
He added, “We hope that the combined efforts of the internet community will help put an end to Semalt’s illicit activity, and help dissuade other services from using this and similar unscrupulous tactics in their business practices.”