Knock Knock Tool
For years Mac OS users have been snug about the fact that there too few malwares and trojans that can harm their Mac OS X. Between these far and few malwares, the Anti-virus that are available for Mac OS X usually identified them and quarantined them. However all this is to prove wrong with what Patrick Wardle has done.
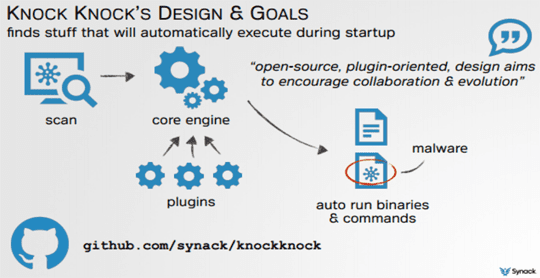
Security research and developer Patrick Wardle has released a tool to reveal executables that automatically boot in Mac OS X. The Knock Knock tool was open source and built on an extensible framework to encourage the community to evolve the platform. You can download the Knock Knock tool from Github here.
Synack’s Patrick, who has released this tool, said he designed the tool because he was concerned about the lack of insight into the potential for persistent malware to load on his OS X machine. He said that his worries were justified given that Apple is giving very “feeble” anti-virus protection and that a further 33 OS X malware families were discovered last year.
“I was really bothered by the fact that I did not know what was automatically executing on my computer or if there was any persistent malware on my computer that I wouldn’t know about it,” Wardle said.
“[Knock Knock] should show me everything that is set to automatically execute when my Mac is rebooted. “I’ve run it on some friends’ computers and actually found a bunch of OS X malware.”
He stated that his studies showed that even a fully patched PC running on Mac OS X was “not that secure” and that the built-in anti-malware mechanisms were “pretty lame” to be trusted for security.
“There [are] tonnes of ways for malware to persist on OS X and Mac malware is certainly a reality, particularly if you’re a Chinese activist or one of my friends who I guess have questionable browsing habits.”
One of the first things the newly released Knock Knock Tool did was to detect the “clipboardd” persistent malware when it listed all binaries unsigned by Apple meaning users needed to have knowledge of OS X malware.
Clipboardd copies Mach-O from its current location to HOME/Library/LaunchAgents/clipboardd and creates a plist file in the same directory with the name com.apple.service.clipboardd.plist.
Wardle said since Knock Knock Tool is open source, Plugins could be added to scan for new persistence techniques to keep it abreast of threats. He also stated that writing the plugins was simple and noted the beta-phase command line tool was stable and usable.
You can watch the video below to know more about Knock Knock Tool