Password Stealer malware stored on Google Drive being delivered to Steam users online
A malware that aims to steal the credentials of STEAM users has cropped up recently. This malware is being spread via the service’s chat feature.
It asks users to click on a link which is shortened using the shortening services available on internet.
When the user clicks on it, it gets directed to a file stored on Google drive. The file appears to be an image file, complete with an image icon on it. This file in fact is an executable and will steal your Steam credentials once executed.
Table Of Contents
Obvious Attack
If you are familiar with malwares, this process would’ve sounded like the most obvious trick in the book.
That’s because it is. But if we are reporting it, it shows that sometimes even the most obvious attacks can get victims. Most gamers are aware of such malware attacks and remain always vigilant enough to stay away from malicious sites.
But at times, people do tend to fall prey as has happened in this case many a times.
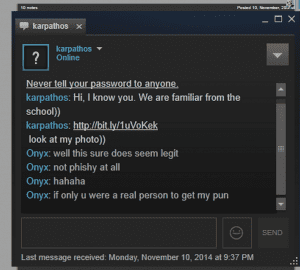
As said above, most of the gamers are aware of the malware laden links being pushed on the chats. Many a times the links become a butt of joke on the Steam chat because lots of gamers are aware of it. Here is a example of one of them.
Bart Blaze, malware researcher at Panda Security, who analyzed the sample and provided a technical overview in a blog post on Sunday explains that the malicious link proceeds to download a screensaver file (SCR extension), which is an executable, from Google Drive; the SCR purports to be a picture and even has an image as the file icon.
“Note that normally, the Google Drive Viewer application will be shown and this will allow you to download the .scr file. In this case, the string ‘&confirm=no_antivirus’ is added to the link, which means the file will pop-up immediately asking what to do: Run or Save. (and in some cases download automatically),” he writes.
Apparently, its too obvious
Now for the good news bit. This attack seems to be so well known that a majority of anti viruses available are known to protect against it.
Most reputable antivirus solutions detect it and prevent its download on the computer. 37 out of 55 antivirus engines on VirusTotal have no trouble quarantining it on the spot.
In the researcher’s analysis, it is noted that the malware connects to a server hosted in the Czech Republic, where the stolen information is probably uploaded.
Signs of the Steam account log-in information compromised via this threat consists in the presence of a process named “temp.exe,” “wrrrrrrrrrrrr.exe,” “vv.exe,” or one with a random name running on the system; this can be checked with Task Manager.
No action seems to have been taken against this malware as the file still exists on Google’s cloud storage service. This is the only reason that Steam users may think it is legit and fall prey to the malware.