Table Of Contents
Regin – the ‘New Stuxnet’ state sponsored espionage tool
A new high grade state sponsored espionage software has surfaced as per Symantec researchers, with experts claiming it is as sophisticated as Stuxnet and probably even more dangerous because of its capabilities. Based on the complexity of it, researcher feel it has the backing of a nation state and with complex resources at hand. Symantec says that this kind of sophisticated malware would mean that the authors/ creators of Regin have dedicated nation state resources required to manage level of complexity and resources to build it.
Mass Espionage
Symantec malware reversers found attackers have foisted Regin on targets using mixed attack vectors including one unconfirmed zero-day in Yahoo! Messenger. “Regin is a complex piece of malware whose structure displays a degree of technical competence rarely seen,” Symantec’s researchers wrote.
“Customisable with an extensive range of capabilities depending on the target, it provides its controllers with a powerful framework for mass surveillance and has been used in spying operations against government organisations, infrastructure operators, businesses, researchers, and private individuals. “It is likely that its development took months, if not years, to complete and its authors have gone to great lengths to cover its tracks. Its capabilities and the level of resources behind Regin indicate that it is one of the main cyber espionage tools used by a nation state.”
The below chart depicts the targets of the spyware :
Researchers have refrained from naming any country as being behind this spyware. Although they did confirm that a majority of its targets resided in Russia and Saudi Arabia and were targeted between 2008 and 2011, with a since-decommissioned version of the malware that re-surfaced after 2013. “Its design makes it highly suited for persistent, long term surveillance operations against targets,” the researchers wrote.
Regin the equivalent of Stuxnet and Duqu
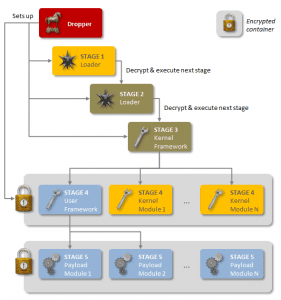
The highly-complex malware was comparable only to Stuxnet and Duqu, researchers said in the report Regin: Top-tier espionage tool and many of its elements were undiscovered. Reign has the capability to add to its spyware with remote access trojans to swipe keystrokes and screenshots, tools to nab information on processes and memory utilization, and others to recover deleted files.
Specialist modules were found monitoring Microsoft Internet Information Services network traffic, parsing mail from Exchange databases, and collecting administration traffic for mobile base station controllers. Regin’s talented authors encrypted data blobs after the stage one vector. The stage zero dropper probably responsible for setting extended attributes and registry keys that held encoded data of subsequent stages was not found. There are also seperate version for 32 bit and 64bit machines.
Technical aspects
As already reported, it’s one of the more complex pieces of malware around, and just like many of the other toolkits it also has a long history behind it. We first encountered Regin nearly six years ago in early 2009, when we found it hiding on a Windows server in a customer environment in Northern Europe. The server had shown symptoms of trouble, as it had been occasionally crashing with the infamous Blue Screen of Death. A driver with an innocuous name of “pciclass.sys” seemed to be causing the crashes. Upon closer analysis it was obvious that the driver was in fact a rootkit, more precisely one of the early variants of Regin.
Symantec researchers noticed the following registry keys being used for the next stage payload:
• \REGISTRY\Machine\System\CurrentControlSet\Control\Class\{9B9A8ADB-8864-4BC4-8AD5-B17DFDBB9F58}:Class
• \REGISTRY\Machine\System\CurrentControlSet\Control\Class\{4F20E605-9452-4787-B793-D0204917CA58}:Class
• \REGISTRY\Machine\System\CurrentControlSet\Control\RestoreList:VideoBase
The following folders containing an NTFS Extended Attribute with the name “_” have also been seen to store the next stage payload, which can actually be split between two different attributes:
• %WINDIR%
• %WINDIR%\security
• %WINDIR%\repair
• %WINDIR%\msapps
• %WINDIR%\msagent
• %WINDIR%\Cursors
• %WINDIR%\fonts
• %WINDIR%\Temp
• %WINDIR%\msagent\chars
• %WINDIR%\Help
• %WINDIR%\inf
• %WINDIR%\Spool\Printers
• %WINDIR%\CertSrv
A final word by researchers is that, although it is next to impossible to determine for sure the origins of a malware in which the creators have put in so much effort to hide their tracks, a few believe that the source has a low possibility of being China or Russia and probably being from a more developed nation from western hemisphere.
‘Regin’ targeted GSM Networks
The layers of the Regin cyber-attack platform are just beginning to be pulled back. One of those layers gives attackers the means to penetrate and monitor GSM base station controllers.
Kaspersky researchers have noticed that Regin had targeted GSM networks also. During its investigation, Kaspersky Lab examined the activity log of a GSM base station controller and discovered that attackers were able to obtain credentials that would allow them to control GSM cells in the network of a large cellular operator.
Kaspersky researches state that this could mean the authors/creators of Regin had complete access to the GSM network and information about what calls are being processed by a particular cell, redirect those calls to other cells, activate neighbor cells and perform other offensive actions. According to Kaspersky Lab, no other attacks are known to have been capable of those types of operations.
“The ability to penetrate and monitor GSM networks is perhaps the most unusual and interesting aspect of these operations,” the Kaspersky Lab researchers note in a whitepaper describing the platform. “In today’s world, we have become too dependent on mobile phone networks which rely on ancient communication protocols with little or no security available for the end user. Although all GSM networks have mechanisms embedded which allow entities such as law enforcement to track suspects, other parties can hijack this ability and abuse it to launch different attacks against mobile users.”
You can read the White Paper published by Kaspersky Lab here.