Samy Kamkar’s ProxyGambit picks up where the defunct ProxyHam left off
Ben Caudill’s scheduled DEF CON demonstration of ProxyHam, a hardware proxy best suited for whistleblowers and others worried about online privacy, apparently got cancelled. On July 10, through his company Rhino Security Labs’ Twitter feed, Caudill announced that not only was his talk canceled, but source code for ProxyHam would not be released, existing devices were being disposed of and all development was at a standstill.
The sudden and unknown demise of the ProxyHam device disappointed the privacy advocates. Caudill has declined to disclose why his talk won’t be given, and while he’s been discouraged in moving forward with his project, others have not.
Effective immediately, we are halting further dev on #proxyham and will not be releasing any further details or source for the device
— Rhino Security Labs (@RhinoSecurity) July 10, 2015
Existing #proxyham units will be disposed of and no longer be made available at @_defcon_
— Rhino Security Labs (@RhinoSecurity) July 10, 2015
Samy Kamkar, a 29-year-old hardware hacker and entrepreneur who in the past seven months has hacked a USB charger to sniff keystrokes over the air and child’s toy to figure out garage door codes, has picked up the cause for devices like ProxyHam. Similar in concept to ProxyHam, Kamkar uncovered ProxyGambit this week at DEF CON and said that his device puts more distance between the user and the device than ProxyHam.
ProxyGambit, is a $235 device that lets people access an Internet connection from anywhere in the world without disclosing their IP address or true location. It’s radio link can offer a range of up to six miles, more than double the 2.5 miles of the ProxyHam. More importantly, it can use a reverse-tunneled GSM bridge that connects to the Internet and exits through a wireless network anywhere in the world, a capability that provides even greater range.
From the site: “While a point-to-point link is possible, the reverse GSM bridge allows you to proxy from thousands of miles away with nothing other than a computer and Internet with no direct link back to your originating machine.”
His approach makes it more hard to find out many times where the original traffic is coming from, as told to Threatpost by Kamkar.
“With ProxyGambit, once someone tracks the IP down, it’s almost a dead-end—it’s the ProxyGambit device using that Wi-Fi’s wireless connection,” Kamkar said. “If they go to the location and find the actual ProxyGambit device, they may find the 2G SIM card—which can be purchased with cash and no tie to your identity, and there’s almost no way to find out who was on the other side. Even if a government asked the mobile company, they’d have no information other than ‘pre-paid user.’”
Kamkar mentions on his site how ProxyGambit can be utilized with either a high speed link with a direct line of site (up to 10 kilometers), or if further away, over a 2G GSM connection that makes a “reverse TCP tunnel serializing a shell into the device” that can be retrieved either over the GSM mobile protocol or Internet. “Either method proxies your connections through local Wi-Fi networks near the device, shielding and making it more difficult to determine your true location, IP and identity,” he says on the site.
He further adds on the site “Either method proxies your connections through local Wi-Fi networks near the device, shielding and making it more difficult to determine your true location, IP and identity.”
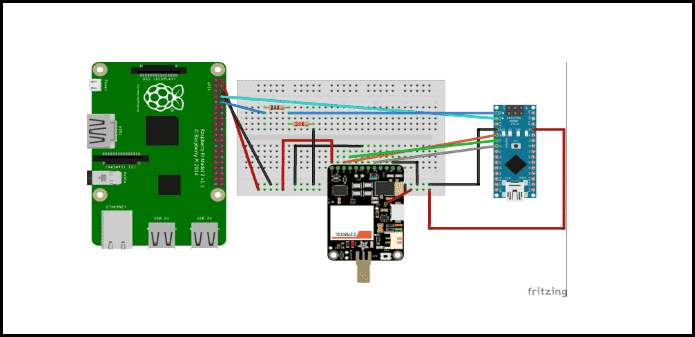
The default hardware making up the ProxyGambit includes:
Raspberry Pi 2 Model B
Powered USB hub
The Adafruit FONA GSM board
A FONA antenna
An ATmega328 Arduino device
3.7 Lithium-Ion (LiOn or LiPo) Battery
point-to-point wireless links (either two Ubiquiti NanoStation LocoM2s , or a pair of the Ubiquiti NanoStation LocoM5s to achieve 10km+ range)
SIM card
SD card
Kamkar said “ProxyHam seemed great, but the range was an issue, and also the fact that line of sight is necessary. Also, it’s trivial to track that strong signal back to the originating antenna (your actual physical location).”
“ProxyGambit improves upon ProxyHam by adding the GSM layer which allows you to be anywhere in the world.”
This is not the first go-round building hardware-based anonymization devices for Kamkar.
“While I’ve built similar systems and gateways like this in the past, I built this specifically after I heard about the cancellation,” Kamkar said. “I thought ProxyHam was a great addition to the arsenal for privacy advocates and wanted it to live on.”
In the meantime, a second ProxyHam alternative has been put forward by Errata Security CEO Rob Graham. “The point of ‘ProxyHam’ isn’t that there is some new magic out there, but that hackers can take existing stuff, for their expected purpose, but achieving an unexpected outcome,” Graham wrote.
While these projects may be worth looking into, however, it’s also vital to keep in mind the privacy and anonymity these devices offer remain largely unproven. In other words, it means people should not depend on them to protect their identity in cases where their life or liberty is at risk at least without doing a thorough testing first.
“This is an insecure, bare bones proof of concept,” Kamkar wrote. “The fragmentation of data through alternate mediums is a useful and effective concept and those interested in privacy, anonymization, or deanonymization should explore this area further. Entropy is both gained and lost with these methods and many risks are involved when deploying any system of this nature.”
More details of Samy Kamkar’s ProxyGambit can be found here.