Table Of Contents
Stagefright vulnerability: How to check if your Android device is affected and remedies to tackle this exploit.
It’s been some weeks since Zimperium, a security company, discovered some six plus one critical vulnerabilities in the native media playback engine called ‘Stagefright’. According, to the security researcher, Joshua Drake, these weaknesses should be termed as ‘Mother of all Android Vulnerabilities’.
It is indeed a big question if one wants to find out if their device has already been affected and if yes, what should be their next step. Suppose, the device is safe, how can one protect the device against this attack. This article will briefly explain all these queries.
What is Stagefright attack?
Basically, Stagefright vulnerability is a sort of weakness which can be exploited by the attackers to take over an Android smartphone by executing malicious codes which would be embedded in a video that is either sent through MMS messages or Google Hangout chat. When user opens this video, the malicious code gets triggered and can infect the device.
Stagefright vulnerability is definitely one of the biggest security concerns to Android because it can be automatically delivered through MMS which allows attacker to remotely control and steal data from the device. Stagefright mostly affects the devices that runs on Android Jelly Bean or its earlier versions. It has been observed that almost 40 percent of overall Android users use KitKat, Jelly Bean or earlier versions.
Ever since Google launched its Android 4.0 Ice Cream Sandwich version; Address Space Layout Randomizing aka ASLR technology too has been a part of Android. In the presence of ASLR technology, the amount of RAM which an app will use would never be the same. Hence according to Google, presence of ASLR technology protects the device from the Stagefright attack.
The problem here is that ASLR technology is not foolproof and it is susceptible to the various nefarious attempts of the attackers to circumvent this protection level. It has already been proved by researchers that Stagefright can be triggered through apps and URLs.
The good news here is that if attackers attempt attack via URL or app, it is possible to avoid it, because one needs to manually retrieve the videos; however in case of MMS the video gets retrieved automatically which is very much dangerous.
Let us understand how to make out if the device has already been attacked by Stagefright?
There are two apps which users can download. These apps will tell user if their phone has been attacked by Stagefright.
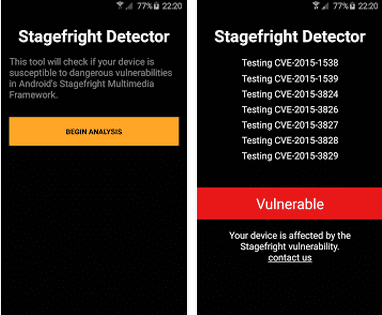
Stagefright Detector App for Android devices (click on the link to download the app)
This app has been developed by Zimperium Inc. This tool detects if the Android device is susceptible to the dangerous vulnerabilities in Android’s Stagefright Multimedia framework. It also detects if there is any need to update your mobile Operating System.
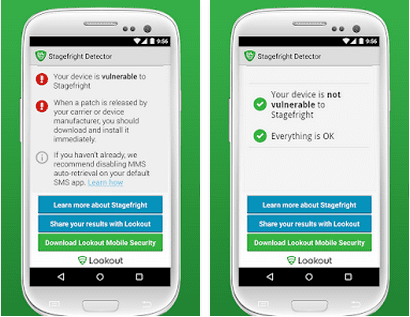
Stagefright Detector App by Lockout Mobile Security (click on the link to download the app)
Lockout Mobile Security designed the Stagefright Detector to keep the user informed about the status of their Android device. Lockout has made it clear that its Stagefright Detector App does not fix the vulnerability.
The Stagefright vulnerability affects any Android device that runs on Froyo 2.2 to Lollipop 5.1.1. It has also been documented with the reference numbers such as CVE-2015-1538, CVE-2015-1539, CVE-2015-3824, CVE-2015-3826, CVE-2015-3827, CVE-2015-3828, CVE-2015-3829.
The vulnerability can be fixed only when Google releases the patch through System Updates which can be delivered via the manufacturer of the device or carrier. Users can check if a patch is available for their device by going to Settings and clicking the System Update button.
Basically, both the Stagefright Detector apps scan the Android device to determine if the device has been affected already and if yes, then they provide the user with advice on how to protect the device and its data. For instance, user can install any patch from their carrier or OEM and disable MMS auto fetch in the device’s default messaging app until the device has been patched.
Well, there is not much that an user can do to stop the Stagefright attack. For now, the sole option is to get into the settings of Messaging app and Turn Off the auto-retrieve mode for MMS and this setting holds good for default Messaging app as well as apps like Hangouts.
User would also need to disable the auto downloads of Whatsapp. For this, go to Settings > Chat Settings > Media Auto Download and then make sure the auto downloads are disabled under these categories as well ‘When using mobile data’, ‘When connected on Wi-Fi’ and ‘When roaming’; these are for auto downloads of videos.
The avoid being exploited by this vulnerability, Android users need to avoid opening any MMS message or any messages and links from any unknown users.
Android smartphones that are getting the Stagefright patch
Several manufacturers have also assured their users that they will issue the Stagefright patch and others will also start releasing the monthly security patches. Enlisted are some of the companies which have either already made an announcement to release the patch or have confirmed the update, it also contains the models which will receive the patch.
Google Stagefright patch: The very first one to announce the Stagefright fix was Google. Android One devices have already been patched and Nexus line of devices, too, would receive the patches and monthly security updates.
- Nexus 6 Android update
- Nexus 5 Android update
- Nexus 4 Android update
- Nexus 9 Android update
- Nexus 7 (2013) Android update
- Nexus 7 (2012)
- Nexus Player
Samsung Stagefright patch: Samsung has also issued a statement about the Stagefright patch and monthly security updates for its popular devices. Sprint and AT&T too have announced to push the patch out for Samsung devices. Though Galaxy S4 and Galaxy S3 are still on the ‘to-do’ list for the patch.
- Galaxy S6 Android update
- Galaxy S6 Edge Android update
- Galaxy S6 Active
- Galaxy S5 Android update
- Galaxy S5 Active
- Galaxy Note 4 Android update
- Galaxy Note Edge Android update
Motorola Stagefright patch: Motorola too has joined the group and announced to patch its devices, which comprises a big list of devices.
- Moto X Style (patched from launch)
- Moto X Play (patched from launch)
- Moto X (2014) Android update
- Moto X (2013) Android update
- Moto X Pro
- Moto Maxx/Turbo Android update
- Moto G (2015)
- Moto G (2014) Android update
- Moto G (2013) Android update
- Moto G 4G LTE (2015)
- Moto G 4G LTE (2014)
- Moto E (2014)
- Moto E (2013) Android update
- Moto E 4G LTE (2015)
- DROID Turbo
- DROID Ultra/Mini/Maxx
LG Stagefright patch : It seems LG has confirmed to Wired that it would provide the updates to its users along with monthly security patches; however it has not made any official statement.
- LG G4 Android update
- LG G3 Android update
- LG G2 Android update
HTC Stagefright patch : HTC has already pushed the patch to several devices though it has not promised any monthly security updates.
- HTC One M9 Android update
- HTC One M8 Android update
- HTC One Android update
Sony Stagefright patch : Similar to HTC and LG, Sony has not made any official statement regarding the patch; however it seems it has issued the patch to few of its devices.
- Xperia Z4
- Xperia Z3 Android update
- Xperia Z3 Compact Android update
- Xperia Z2 Android update
Readers, hope this article has answered some of your questions. Stay tuned for more news regarding Stagefright attack.