Table Of Contents
Security researchers discover novel methods of stealing secret data from computer by hacking modern devices
New methods have been discovered by security researchers wherein they just need to infect devices such as printers, airconditioners or washing machine and turn it into a radio!
Researchers at Red Balloon Security, a Manhattan start up, have discovered ways to steal crucial files from computers by just infecting devices such as printer, air conditioner or washing machine.
Just imagine, this novel method would enable hackers to steal crucial data even from military bases or nuclear facilities or from computers which are not connected to Internet! Security researchers claim that hackers can steal the data without setting off any alarm!
This sounds unbelievable and too much of a science fiction! However, security researcher Ang Cui and his brilliant team have just demonstrated this mind boggling method to several reporters in a press conference last week.
Converting modern device into a radio to broadcast the data:
According to Cui, hackers do not have to rely on Internet to pull essential data from computers.
Instead, hackers simply need to hack some modern office device such as printer or air conditioner or even a washing machine.
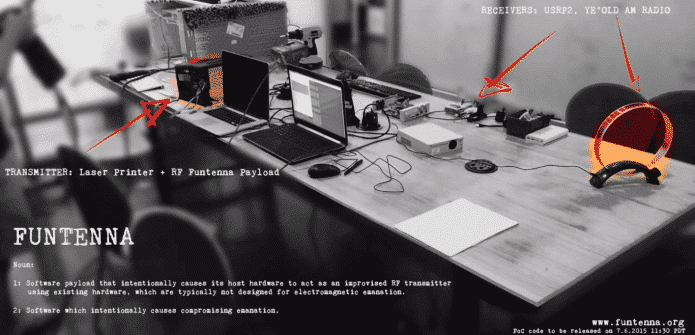
During the demonstration, the team infected a Pantum laser printer and fiddled with its circuit due to which the printer was converted into a radio and started broadcasting invisible and inaudible signals which could be picked up by hackers placed several miles away.
The researchers actually swapped the chip’s energy output in such a manner that the printer started emitting electromagnetic radiations.
Now, if this swapping was done at a bit slower pace, one would be able to hear some coarse sound. However suppose one cranks it way up then the printer starts giving radio waves.
These highs and lows together form the 1s and 0s, which is the basis of computer code.
Red Balloon Security team have named this as “Funtenna”.
This entire process is quite slow, one can expect to get a single letter per second. However, Cui says that one can use thick cables which can act as amplifier to speed up the process. The cables need to be like those which are found in enormous computer rooms.
This indirectly indicates that a hacker can effectively pull vast data from computers which has an abode of essential data.
Cui says: “You have network detection, firewalls… but this transmits data in a way that none of those things are monitoring.”
He added: “This fundamentally challenges how certain we can be of our network security.”
According to Cui, this is an advanced method of hacking and this sort of data theft can be detected only if one manually walks in the facility holding an AM radio.
Cui also explained that suppose if a device has been hacked and is stealthily transmitting the radio signals, then the radio static gets interrupted by these secret emissions from the device which is indicated by a loud beep in the AM radio.
Now, this is indeed an innovative idea which will change the future of hackers. At the same time this sort of advancement in the hacking systems would mean that the cyber security industry which is involved in guarding the computer networks too will have to discover means to safeguard themselves from such technologies.
Already the cyber security industry is expanding rapidly and various government organizations as well as companies are buying products to safeguard themselves from the cyber attackers; however hackers seem to be a step ahead of the defensive options!
Security researcher, Cui and his team plan to present their findings at the Black Hat hacker conference which would be held this week in Las Vegas.