Table Of Contents
Hacking Team hack attack seems to be pushing FinFisher malware sales among governments
Don’t know about FinFisher? Let us say that after reading about this, you will be curious to know much more
FinFisher, the notorious spyware used for malicious activities is increasing in popularity amongst government agencies. To date, 32 countries have been identified as active users of the spyware. For those of you who are not familiar with the program, FinFisher is sold exclusively to government agencies and police forces, meaning that regular individuals are definitely not a part of the clientele. The spyware is extremely easy to use and is highly effective in fulfilling its purpose, which at this point, happens to be remotely controlling any computer in the world that it ends up infecting.
That is not all that the program is capable of. FinFisher is also capable of intercepting your Skype calls and log keystrokes, and that is just tip of the iceberg. The program was developed by FinFisher Gamma Group, which is currently located in Munich and the primary aim of the software was to identify threats in the form of serious criminals and help law enforcement agencies and governments to locate and catch them.
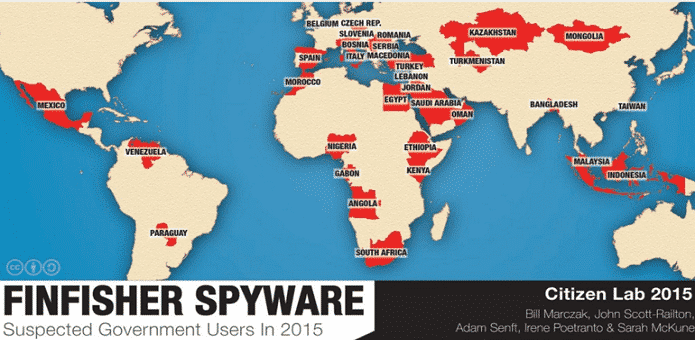
However, nothing is what it actually appears to be because according to the latest data breach, governments were using FinFisher to perform their own clandestine activities. This included keeping a track on high-profile Bahraini activists, as well as law firms, journalists and political opposition located in the region. According to Citizen Lab, which is a laboratory based at the University of Toronto, and has dug deep into global security and human rights issues, the following has been stated about FinFisher:
“Despite the 2014 FinFisher breach, and subsequent disclosure of sensitive customer data, our scanning has detected more servers in more countries than ever before. In presenting our scan results, we do not wish to disrupt or interfere with legitimately sanctioned investigations or other activities. Instead, we hope to ensure that citizens have the opportunity to hold their governments transparent and accountable. Intrusion software presents a challenge for accountability in any country, and the oversight authorities in under-resourced countries facing domestic or international security threats may be particularly ill-equipped in expertise and political clout, to identify or act on signs of misuse.”
The Citizen Lab team devised to plot to uncover the activities of government agencies. During the unravelling of their search, the following agencies were found using the software:
• Directorate General of Forces Intelligence (DGFI) from Bangladesh
• Egyptian Technology Research Department (TRD)
• National Encryption Body (Lembaga Sandi Negara)
• Multiple agencies in Italy
• Kenyan National Intelligence Service (NIS)
• Lebanese General Directorate of General Security and Internal Security Forces (ISF)
• Mongolia’s Special State Security Department (SSSD)
• Moroccan Conseil Superieur De La Defense Nationale (CSDN)
• Serbia’s Security Information Agency (BIA)
The revelation of this data breach led to the creation of The Wassenaar Arrangement, which states that cybersecurity weapons will be within weapon export controls, and includes programs such as FinFisher. However, if data breaches like this would not have occurred in the first, then governments could continue using it to fulfill their own agenda. Even now, we are confident that not all the information has been sifted by the research company, which only means that several agencies will be using the spyware to its maximum potential.