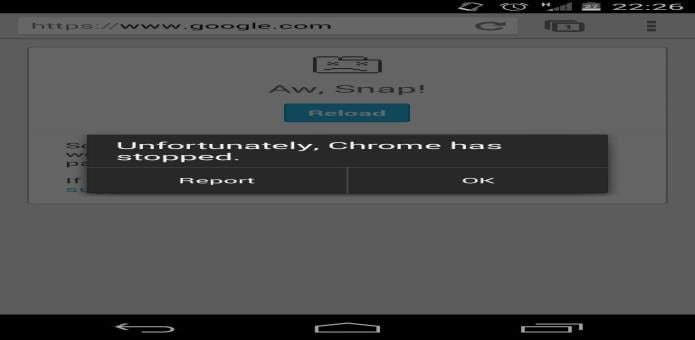
Specially crafted URL crashes Chrome for Android App due to improper handling of intent parameter
If you were to open the below-given URL in your Chrome browser on Android smartphones and tablets, Chrome will crash.
intent://editbookmark/#Intent;scheme=chrome;end
This bug was discovered by an Indian security researcher, Akshay C.S. and is caused to improper handling of intent parameter by Chrome for Android.
This issue is similar to an issue where 16 special characters could crash Chrome Browser on Windows PCs and Laptops. Though the bug discovered by Akshay is not as serious as the special character bug, it can bring down the Chrome browser in Android smartphones and tablets.
Like the special character bug, this bug instantaneously crashes Chrome browser in Android and can be used for pranks. According to Akshay, this bug affects Chrome running on only the Android platform while Chrome on other platforms remains unaffected.
To try this yourself, fire up Chrome 46 or below and click the link below/enter “tinyurl.com/chromecrashes” from Chrome browser on Android. [Note: tinyurl.com seems to be offline at several times, if that doesn’t work, click the link mentioned below].
A big difference between the special character bug and this one is that the previous bug crashed the browser by just hovering the cursor over the link while this one won’t crash the browser unless you explicitly click on the link or enter it in the browser’s address bar. This is because the link doesn’t contain any special characters or sequences that’ll crash.
Akshay says that this crash bug affects all versions including Version 46.0.2490.76 and below. At the time of writing, this is the latest stable version available. Thus this affects all versions of Chrome so far released for Android (at the time of writing this).
Akshay has filed a bug report on crbug.com (Issue 555925) on November 14, and by the day 3 after filing this, this was fixed internally in the code (Thanks, Google!), but the fix will only be available with the next Chrome Release update.
as said above, the bug can be used by pranksters to crash browsers on friends’ Android smartphones. 301/302 the link with the help of a URL shortening service like tinyURL and you’ll get a link that’s indeed a valid URL like https://tinyurl.com/check-this-magic that can be used to crash. Send it to a Nexus owner/Chrome user in a chat, and he/she will be confused at what’s happening!
Why is this happening?
According to Akshay, when you enter the above URL in Chrome or click on it, it sends out (or broadcasts) an intent, which targets chrome. What’s an Intent?, if you ask, then from this wiki:
In Android, the OS or an application can send out a broadcast message that can be monitored by any application. For example, the Android OS sends out broadcast messages about the device, such as if the device has a low battery or changes to airplane mode, while an application can send out a custom broadcast message.
The application can use broadcast receivers to monitor system events from the Android OS as well as custom broadcasts sent by other applications. The application will need to know the name of the broadcast actions in order to monitor them.
From the link, the receiver that is targeted is Chrome, Akshay used scheme=chrome in that intent. This intent is monitored (received) by Chrome handler, and Chrome tries to handle it triggering the activity that’s mentioned here (editbookmark).
The Android crash log output made it clear:
java.lang.RuntimeException: Unable to start activity ComponentInfo{com.android.chrome/org.chromium.chrome.browser.bookmark.ManageBookmarkActivity}: java.lang.NullPointerException: Attempt to invoke virtual method 'long java.lang.Long.longValue()' on a null object reference
Android security team acknowledged the bug and has issued a fix which will be available in the next release of Chrome for Android.
The following revision refers to this bug: https://chromium.googlesource.com/chromium/src.git/+/ad512bd1b580da482a1e773f263f4c530989f740 commit ad512bd1b580da482a1e773f263f4c530989f740 Author: tedchoc <[email protected]> Date: Wed Nov 18 02:14:35 2015 Remove the ability to trigger the edit bookmark dialog via URL. We have long long since moved to a native ntp and trigger it via a direct intent, so we can remove this logic and clean up the intent param handling to avoid invalid data. BUG=555925 Review URL: https://codereview.chromium.org/1452323003 Cr-Commit-Position: refs/heads/master@{#360264} [modify] https://crrev.com/ad512bd1b580da482a1e773f263f4c530989f740/chrome/android/java/AndroidManifest.xml [modify] https://crrev.com/ad512bd1b580da482a1e773f263f4c530989f740/chrome/android/java/src/org/chromium/chrome/browser/bookmark/ManageBookmarkActivity.java
You can read the full report here: https://code.google.com/p/chromium/issues/detail?id=555925
Sadly, Akshay was not eligible for Android bug bounty as the Google engineers deemed it to be a DOS vulnerability.