Mac FileVault2 Passwords Can Be Stolen With This $300 Device
You can now use a $300 device to recover login passwords for Macs that are protected by Apple’s FileVault2 disk encryption system.
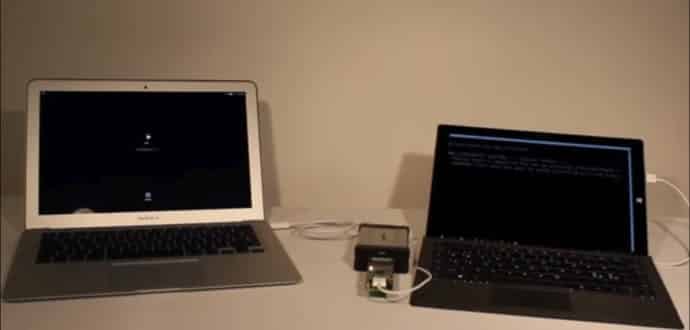
Ulf Frisk, a Swedish hardware hacker has published instructions on GitHub for those users who are interested to build this $300 device known as PCILeech. This device, which only runs on Windows 7 and Windows 10 PCs, uses custom software, and can be used to carry out Direct Memory Access (DMA) attacks, which let an attacker to read the memory of 64bit-based operating systems such as Linux, macOS, FreeBSD, and Windows. The device also runs on a custom hardware rig, and the same GitHub repo offers the list of required components.
Apple FileVault2 design bugs exposed devices to PCILeech
This summer Frisk discovered two design flaws in how Apple applied FileVault2 Mac disk encryption. He integrated these two bugs in version 1.3 of PCILeech, capable of pulling out Mac passwords in cleartext, says the researcher.
The first problem he discovered is that a Mac’s EFI, the homologue of a Windows BIOS/UEFI, opens Thunderbolt 2 ports before the operating system has had a chance to boot.
An attacker can use these Thunderbolt 2 ports to connect devices that can read a Mac’s memory before the operating system starts, at which moment macOS starts anti-DMA protections, stopping his attack from working, says Frisk.
FileVault2 / logon password stored in memory in cleartext
In normal conditions, this wouldn’t be a huge issue, but Frisk says he also found out that before macOS starts, the FileVault2 password (which also doubles as the Mac’s logon password) is stored in the computer’s memory in cleartext.
“The FileVault password is […] not automatically scrubbed from memory once the disk is unlocked,” said Frisk, which means the password lingers around after the user has authenticated.
“The password is put in multiple memory locations,” Frisk adds, “which all seems to move around between reboots, but within a fixed memory range.”
This has allowed Frisk to make a special set of operations for PCILeech in that short interval of time before the macOS anti-DMA protection take effect, that keeps a watch on that memory range, recognizes the password and pulls it out after the Mac reboots.
PCILeech attack takes 30 seconds
The attack takes less than 30 seconds to work, which is possible only if an attacker has physical access to a Mac or MacBook, says Frisk.
A YouTube video shown below shows Frisk executing the attack in less than a minute, but he was moving slow and giving verbal instructions.
Issues fixed in macOS 10.12.2
Frisk contacted Apple last July, when he found the problems and reported the company of his findings.
The issues which Frisk reported were addressed by Apple in macOS 10.12.2 patch released on Tuesday, December 13.
“The solution Apple decided upon and rolled out is a complete one. At least to the extent that I have been able to confirm,” Frisk said. “It is no longer possible to access memory prior to macOS boot. The Mac is now one of the most secure platforms with regards to this specific attack vector.”
A similar device called PoisonTap was created by hardware hacker, Samy Kamkar in November, which can remove passwords, install backdoors on password-protected Windows computers and takeover web traffic.
Source: bleepingcomputer