WannaCry lookalike encrypts files on Android smartphones’ external storage
It looks like the WannaCry ransomware has become a source of inspiration for many crooks around the world. We had recently reported how a 14 year-old teenager from Japan impressed by the malware was arrested last week for developing a malware similar to the WannaCry malware.
Now, cybercriminals in China have developed an Android ransomware that uses similar graphics of WannaCry and trick users into quickly paying the ransom.
For those unfamiliar, WannaCry ransomware exploited a weakness in Microsoft’s Windows operating system and went on to infect more than 3,00,000 computers in 150 countries within 72 hours last month. The WannaCry ransomware cryptoworm encrypted data and demanded payment in virtual currency Bitcoin in exchange for a password to unlock data.
Spotted first by Chinese security firm Qihoo 360 and dubbed as “ WannaLocker ” by Avast, this lookalike version of WannaCry ransomware and is currently targeting Android users living in China. The hackers are spreading this ransomware via Chinese gaming forums where it is disguised as a plugin for the King of Glory, a very popular mobile game in China.
How does the malware work?
Upon installation of this fake add-on in the device, the WannaLocker ransomware hides its app icon from the app drawer and changes the main wallpaper on the infected device to an anime image. Then, it starts encrypting the files stored on the infected device’s external storage.
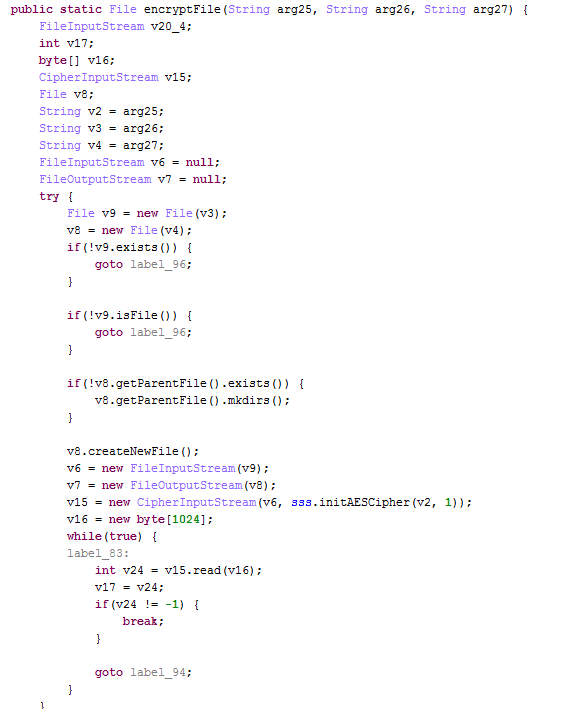
The ransomware uses AES encryption to lock the files (see code below). To prevent corruption and crashing of the Android OS, it doesn’t not encrypt files that begin with a “.”, or files that include “DCIM”, “download”, “miad”, ”android” and “com.” in the path, or files that are bigger than 10 KB.
Once the encryption process is completed, it demands ransom even less than Simplocker, and uses a ransom message clearly inspired by WannaCry’s note to reveal its orders.
Nikolaos Chrysaidos, head of mobile threat intelligence and security at Avast, explains more in a blog post:
“The ransomware then demands a ransom of 40 Chinese Renminbi, which is equivalent to about 5-6 US dollars. This is not much compared to what other mobile ransomware has demanded in the past. The fact that the ransom is being demanded in regular currency and not in cryptocurrencies makes me think the people behind this are trying to make money, and fast. This is, however, risky as the money can be easily traced, unlike when sending cryptocurrencies.”
The victims of the ransomware are instructed to pay the ransom in regular currency using Chinese payment methods like QQ, Alipay and WeChat.
The sloppy handling of ransom suggests that it could be a work of an amateur hacker or group of hackers. As a result, it is just matter of time for the Chinese authorities to find out who are behind the WannaLocker ransomware and who is receiving the ransom.
Here’s a security advice from Avast for Android users:
To protect your phone and valuable photos, videos, contacts stored on it from ransomware, make sure you frequently backup your data and install antivirus on all of your devices.
Additionally, Android users should refrain from downloading apps on any app marketplaces other than Google Play. In case, you become a victim of a ransom-based attack, don’t give into the ransom demand and seek professional help instead.
Last week, Check Point, an online security firm, had detected a malicious malware called “ Fireball ” that was created by Chinese ad corporation Rafotech that takes control of the user’s web browser and generates fake advertisement clicks and promotions for its clients online. The malware affected more than 250 million computers around the world, with India being the worst hit.
Source: IBT