The World Health Organisation (WHO) recently declared the coronavirus outbreak as a ‘global pandemic’ prompting users all over the world to keep an eye on it. However, hackers are using this situation to their advantage to spread malware and steal user information on your computer.
According to a new report from a security firm called Reason Labs, hackers are abusing the dashboards made by several organizations to keep track of COVID-19 to inject malware into computers.
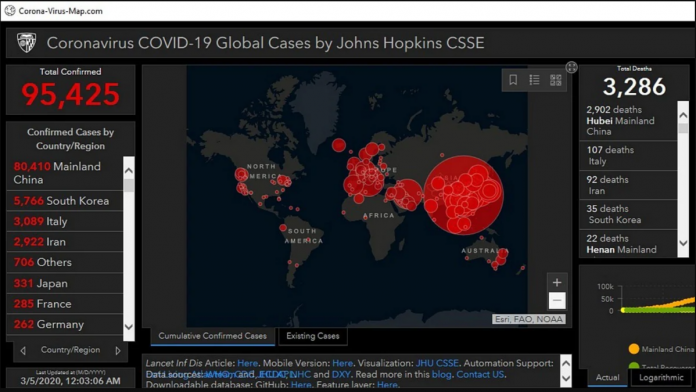
For those unaware, several organizations including John Hopkins University have created dashboards to keep tabs on the spread of the coronavirus. People are dependent on these dashboards to stay up to date with the latest infection numbers.
Attackers are using the coronavirus maps displayed in live tracking to steal information including user names, passwords, credit card numbers and other sensitive information that is stored in the users’ browser.
“As global awareness of a Coronavirus pandemic gradually gives way to full out panic, and as governments begin ramping up their efforts to combat the virus and protect its citizens, global news agencies find themselves racing to answer the public’s demand for accurate information about new Corona related infections, deaths, transmissions, etc,” wrote Reason Labs cybersecurity researcher Shai Alfasi in a threat analysis report.
“This demand creates a vulnerability that malicious actors have quickly taken advantage of by spreading malware disguised as a “Coronavirus map”.”
According to Alfasi, hackers can use this information for many other operations as well, such as selling it on the deep web or for gaining access to bank accounts or social media.
Attackers are designing websites related to coronavirus, which prompt the users to download an application to track the situation of the outbreak. These applications pose as genuine maps that are tracking the viral outbreak, but then installs a malicious binary file dubbed as ‘AZORult’ on the victim’s computer.
AZORult, which was first discovered in 2016 steals browsing history, cookies, ID/passwords, cryptocurrency and more. It can also download additional malware onto infected machines. At present, it is being sold in Russian underground forums with the sole purpose of collecting sensitive data from an infected computer.
A new variant of AZORult, according to reports, creates “a new, hidden administrator account on the infected machine in order to allow Remote Desktop Protocol (RDP) connections.”
Currently, the malware only affects Windows machines but Alfasi expects hackers may develop a new version soon to affect other operating systems as well.
“The malware uses a few layers of packing as well as a multi-sub-process technique to make research more difficult. As the coronavirus continues to spread and more apps and technologies are developed to monitor it, we will likely be seeing an increase in corona malware and corona malware variants well into the foreseeable future,” Shai Alfasi concluded.
To avoid the malware, it is advisable to stick to verified COVID-19 tracking maps and to double-check the URL of a linked website before clicking. Also, refrain from downloading any email attachment from an unknown source. For those who are interested in staying updated on the outbreak, can follow the actual map on John Hopkins University.
Last month, we had reported how cybercriminals used the fear of coronavirus outbreak to launch email campaigns to infect users’ systems with malware.