Researchers at cyber-security firm Forcepoint have discovered that a hacker silently hijacked D-Link NVRs (network video recorders) and NAS (network-attached storage) devices into a botnet in order to download anime (Japanese animation) videos, reports ZDNet.
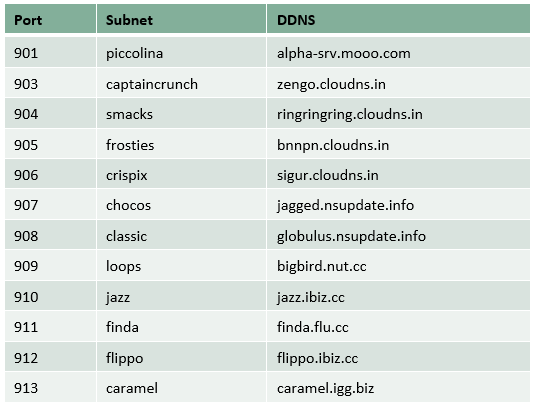
The botnet named “Cereals” was first spotted in 2012 and reached its peak in 2015 when it collected more than 10,000 bots connected to online websites for downloading anime videos. The researchers named the botnet ‘Cereals’ after the naming convention of its subnets.
A detailed report explaining the working of Cereals botnet has been published by Forcepoint.
Despite its size, the botnet went mostly undetected for 8 years from most cyber-security firms because it exploited just one vulnerability in NAS and NVR devices.
Suggested: Best Websites To Watch Anime Online
According to Forcepoint, the hacker scanned the internet for NAS and NVR devices that are vulnerable to this bug and exploited the security flaw to install the Cereals malware.
The bug existed in the SMS notification feature of the D-Link firmware that powered the company’s line of NAS and NVR devices. It allowed the Cereals author to send a malformed HTTP request to a device’s built-in server and execute commands with root privileges.
Cereals botnets used as many as four backdoor mechanisms to access infected devices. However, the hacker patched the infected systems to prevent other attackers from taking over the systems, and also managed infected bots across twelve smaller subnets.
Despite the botnet was quite advanced, the Cereals author never exploited it to access bank accounts or steal personal information or execute DDoS attacks or access user data stored on the NAS and NVR devices.
This implies that the botnet’s author had no criminal motives and that the botnet was actually a hobby project with the only purpose of downloading anime videos from several websites.
“We were also hoping for exceptions amongst the heaps of Anime related requests, but either there is none, or it wasn’t routed through our honeypots. We had to conclude that this is either a simplistic Hobby-VPN-Based-Web-Crawler project of someone or there is a hidden agenda behind the scenes that we lack the evidence of,” Forcepoint researcher Robert Neumann wrote.
Forcepoint’s investigation found that the first wave of exploitation attempts was logged from an IP address in Germany, which is the most likely country of origin. Besides this, all they could find was a name: Stefan.
The security firm describes Stefan as, “a highly motivated individual with good understanding of embedded devices, Linux systems and script programming” who exhibited, “how simply it is to exploit a well-documented vulnerability while cleverly picking a target which is ideal for the purpose and where malicious code can reside undetected for a long period of time.”
The details of the Cereals botnet have been revealed now because the anime-harvesting botnet has slowly disappeared over time, mainly because the vulnerable D-Link NAS and NVR devices are being withdrawn by their owners. And, also because a ransomware strain named Cr1ptT0r removed the Cereals malware from several D-Link systems during 2019.
Also Read- Best Anime Torrent Websites