Researchers at McAfee’s Mobile Research Team have discovered a new malware, dubbed HiddenAds, on the Google Play Store, which disguises itself as a system cleaner to delete junk files on devices or one that can help optimize battery life for device management.
The infected apps hide and promote themselves aggressively on Facebook showing continuous advertisements to victims in a variety of ways. When this malware is installed on the victim’s device, they run malicious services automatically upon installation even without needing any user interaction to open the apps.
To promote these apps to new users, the malware authors created advertising pages on Facebook, as it is the link to Google Play distributed through legitimate social media, leaving little margin for doubt for the users.
The adware apps abuse the Contact Provider Android component, which allows the transfer of data between the device and online services. For this, Google provides ContactsContract class, which is the contract between the Contacts Provider and applications.
“In ContactsContract, there is a class called Directory. A Directory represents a contacts corpus and is implemented as a Content Provider with its unique authority. So, developers can use it if they want to implement a custom directory. The Contact Provider can recognize that the app is using a custom directory by checking special metadata in the manifest file,” McAfee wrote in a blog post.
“The important thing is the Contact Provider automatically interrogates newly installed or replaced packages. Thus, installing a package containing special metadata will always call the Contact Provider automatically.”
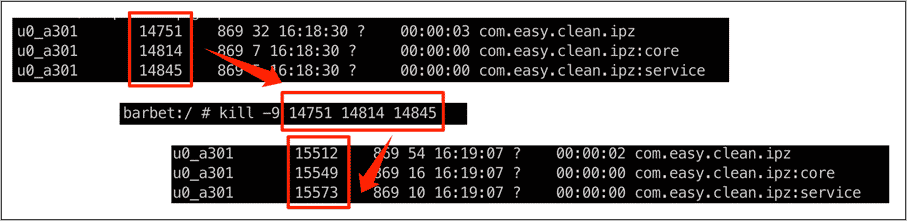
The first activity of this malware is to create a permanent service for displaying the advertisements. If the service process is “killed” (terminated), it regenerates immediately.
Next, they change their icons and names using the <activity-alias> tag to hide.
According to McAfee, users have already installed these apps from 100K to 1M+. Given below is the list of unusually high download numbers for such applications:
- Junk Cleaner, cn.junk.clean.plp, 1M+ downloads
- EasyCleaner, com.easy.clean.ipz, 100K+ downloads
- Power Doctor,power.doctor.mnb, 500K+ downloads
- Super Clean, com.super.clean.zaz, 500K+ downloads
- Full Clean-Clean Cache, org.stemp.fll.clean, 1M+ downloads
- Fingertip Cleaner, com.fingertip.clean.cvb, 500K+ downloads
- Quick Cleaner, org.qck.cle.oyo, 1M+ downloads
- Keep Clean, org.clean.sys.lunch, 1M+ downloads
- Windy Clean, in.phone.clean.www, 500K+ downloads
- Carpet Clean, og.crp.cln.zda, 100K+ downloads
- Cool Clean, syn.clean.cool.zbc, 500K+ downloads
- Strong Clean, in.memory.sys.clean, 500K+ downloads
- Meteor Clean, org.ssl.wind.clean, 100K+ downloads
Most of the affected users belong to countries like South Korea, Japan, and Brazil. McAfee has already disclosed this threat to Google and all reported applications were removed by the search giant from the Play Store.
In case, if you have any of the aforementioned apps installed on your Android smartphone, it is recommended to uninstall them manually from the device.