Security researchers have discovered a extremely critical and high risk defect in the cryptographic software library called OpenSSL. The OpenSSL is used by approximately two-thirds of Web servers use to identify themselves to end users and prevent the leaking or snooping of passwords, banking credentials, and other sensitive data. Potential cybercriminals and attackers who can exploit the vulnerability can monitor all data passed between a service and client, or decrypt historical encrypted data with criminal intent. Many modern operating systems use vulnerable versions of Open SSL including Debian Wheezy, Ubuntu 12.04.4 LTS, CentOS 6.5, Fedora 18, OpenBSD 5.3, FreeBSD 8.4, NetBSD 5.0.2 and OpenSUSE 12.2. In addition two of the most widely used web servers, Apache and nginx and most of the email servers and chat services, VPN etc. use this code library. Other than the above, most of the devices that use embedded Linux like routers etc are also susceptible to this vulnerability.

The flaw which resided in the production versions of OpenSSL for two years since December 2011 could mean that hackers/attackers could recover the private encryption key in the digital certificates. This could then be used to authenticate the data travelling between the servers and the end users making it easy for cyber criminals to exploit almost all user credentials like email ids, passwords, banking user names and passwords etc.. The bug did not leave the traces of the attack in the server logs so nobody could know if their servers were compromised neither did the end users know if they were being subjected to any id theft.
The announcement of the bug in OpenSSL coincided with the release of version 1.0.1g of Open SSL. It has been given a nickname ‘Heartbleed’ to emphasize that the bug was indeed at the heart of the OpenSSL. The old versions of OpenSSL viz 1.0.1 through 1.0.1f with two exceptions: OpenSSL 1.0.0 branch and 0.9.8 are still vulnerable.
CloudFlare, a CDN service provider stated on its blog that it already knew about the vulnerability and hence took step to prevent any compromise with CloudFlare backed servers.
Today a new vulnerability was announced in OpenSSL 1.0.1 that allows an attacker to reveal up to 64kB of memory to a connected client or server (CVE-2014-0160). We fixed this vulnerability last week before it was made public. All sites that use CloudFlare for SSL have received this fix and are automatically protected.
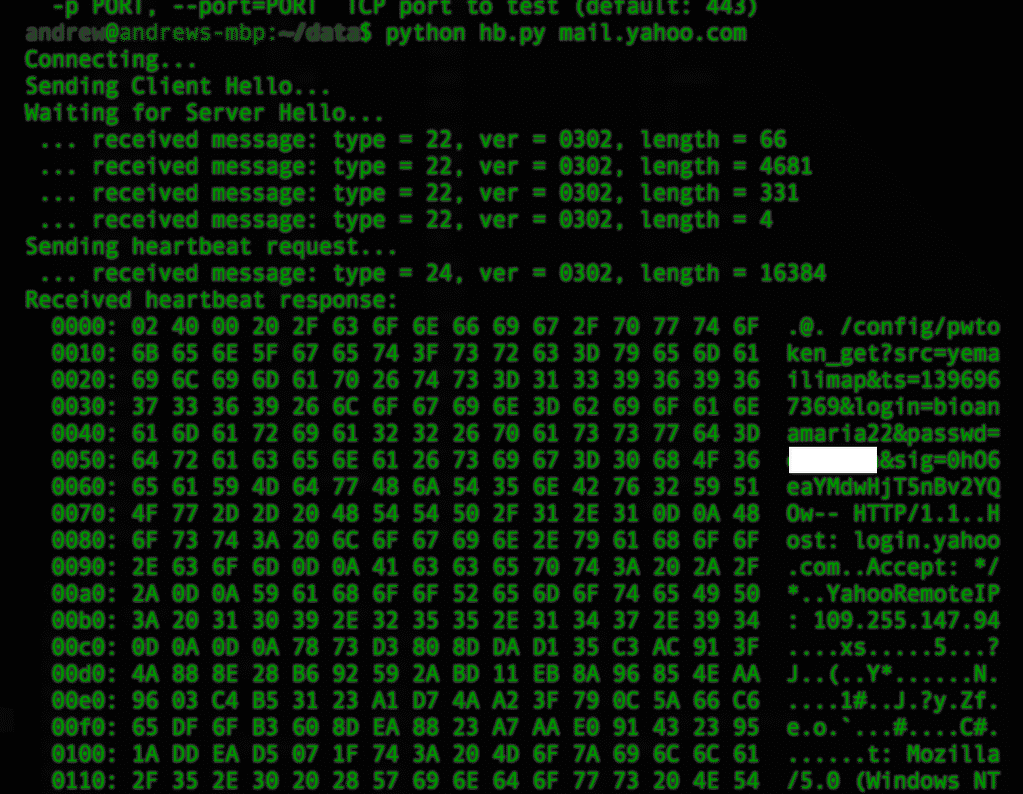
A security analyst, Jared Stafford has released a Python testing code for this vulnerability. The PDF file of the Python Tester is given below for your reference.
Update: As soon as the Vulnerability was released online the Internet has started bleeding leaks. hundreds of top thousand websites Including yahoo, Microsoft, Ubuntu, FBI, Baking websites, Government websites and payment Gateways have been found vulnerable and hackers have already started attacking and leaking User credentials from Many of the websites.
Some other websites including ebay were quick and fixed the vulnerability saving themselves from bleeding the user credentials several other websites are going down to fix the vulnerability, so if you see some of the Major websites going down for a maintenance in next few hours its not a big deal unless leaks from their server goes online before that.
The best way to stay secure is, not to login on any online service vulnerable to heartbleed until the system admin fix it.