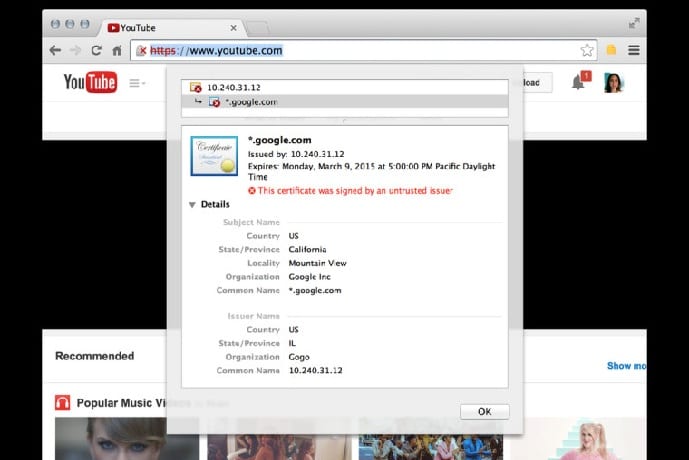
Recent reports have confirmed that Gogo Inflight Internet have been intentionally issuing fake SSL certificates effectively performing man-in-the-middle attacks on its own users.
The security compromise was detected by a Google Chrome security engineer named Adrienne Porter Felt who discovered this during a flight she took while using the inflight service provided by Gogo Inflight Internet. She noticed this while connecting to Google sites and looking at the issuer of the SSL certificate. The SSL certificate was being issued by Gogo and not Google.
This serious man-in-the-middle attack is likely to have effected all user sessions that Gogo Inflight Internet provide service for including Aeromexico, American Airlines, Air Canada, Japan Airlines and Virgin Atlantic, possibly many others.
It was also revealed through the FCC that Gogo has partnered with government officials to produce “capabilities to accommodate law enforcement interests” that go beyond those outlined under federal law. Working closely with law enforcement by directly injecting spyware into their inflight service.
It is now known that Gogo is now intentionally attacking its user’s browsing sessions directly to remove any line of defense that a user may have. This makes it suspect that this is not being done for any legitimate reason.
Based on these facts Gogo is wittingly cooperating with governments and law enforcement groups, including undisclosed “third parties” heavily it mining its customer’s data
Gogo also offers in-flight texting and voice mail, and there is a high probability that Gogo is miss-handling the privacy and security elements of those as well.
If you have used Gogo service at all, it is highly probable that all of your communications, including those over SSL/TLS, have been compromised and you immediately reset your passwords. If you must use Gogo’s service in the future, do so through the use of Tor and/or through a secure VPN.
SSL/TLS Explanation:
SSL/TLS is a protocol that exists to ensure there exists an avenue for secure communication over the Internet. Through the use of cryptography and certificate validation The use of SSL certificates make man-in-the-middle attacks (where a third party would be able monitor your internet traffic) difficult to carry out. Secured transmissions for sensitive data like credit card numbers and user account passwords becomes significantly safer.
A man-in-the-middle attack would require the attacker to attack and emulate the SSL certificate before being able to snoop on a user’s traffic.