Security Researchers detect ‘Destover’ Malware with Stolen Certificate from Stolen Sony Pictures
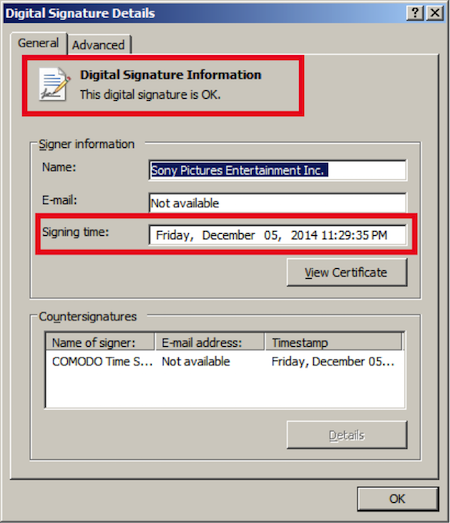
Security researchers at Kaspersky have detected strains of the malicious Destover malware in the wild. The surprising part is that the strains had a digital certificate which the researchers believe was stolen from the high profile #GOP hack attack on Sony Picture corporate network.
This means the the hackers behind the Sony Pictures hack attacks are now leaking digitally signed Sony Pictures certificates to cyber criminals. This may be done for a price according to report.
So what does this mean? The stolen Sony certificates (which were also leaked by the attackers) can be used to sign other malicious samples. In turn, these can be further used in other attacks. Because the Sony digital certificates are trusted by security solutions, this makes attacks more effective. We’ve seen attackers leverage trusted certificates in the past, as a means of bypassing whitelisting software and default-deny policies, Kaspersky researchers noted on their blogpost.
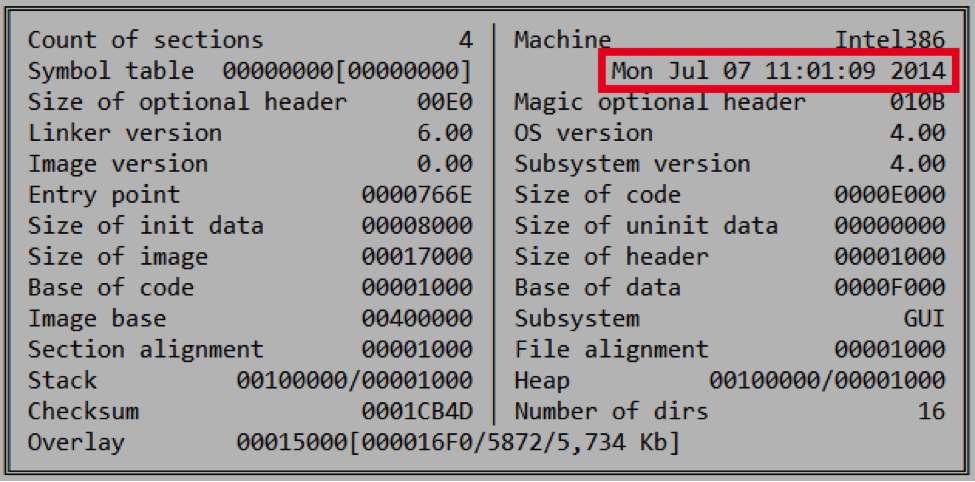
As per the image above, the certificate which has been obtained by Kaspersky has been signed on December 5, 2014 and the Sony hack attack occurred in last week of November, 2014 which means that there may be more malware which come signed with certificates of Sony Pictures in near future. The old certificate which previously observed is a non signed form, as MD5: 6467c6df4ba4526c7f7a7bc950bd47eb and appears to have been compiled in July 2014.
The Sony hack attack is so massive that it has leaked unreleased Sony movies, the salary, ssn and other personal details of Sony employees and Hollywood celebrities and now the presence of digital certificate in a malware points to the fact that the aftershocks of the #GOP hack may be far from over.